What is the function of an assembler
What is the function of an assembler
Introduction of Assembler
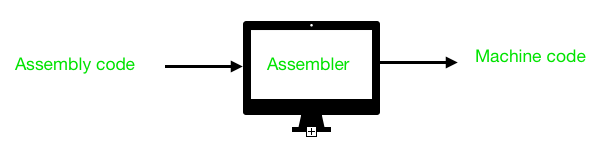
Assembler is a program for converting instructions written in low-level assembly code into relocatable machine code and generating along information for the loader.
It generates instructions by evaluating the mnemonics (symbols) in operation field and find the value of symbol and literals to produce machine code. Now, if assembler do all this work in one scan then it is called single pass assembler, otherwise if it does in multiple scans then called multiple pass assembler. Here assembler divide these tasks in two passes:
Firstly, We will take a small assembly language program to understand the working in their respective passes. Assembly language statement format:
Let’s take a look on how this program is working:
Working of Pass-1: Define Symbol and literal table with their addresses.
Note: Literal address is specified by LTORG or END.
Step-1: START 200 (here no symbol or literal is found so both table would be empty)
Step-2: MOVER R1, =’3′ 200 ( =’3′ is a literal so literal table is made)
| Literal | Address |
|---|---|
| =’3′ | – – – |
Step-3: MOVEM R1, X 201
X is a symbol referred prior to its declaration so it is stored in symbol table with blank address field.
| Symbol | Address |
|---|---|
| X | – – – |
Step-4: L1 MOVER R2, =’2′ 202
L1 is a label and =’2′ is a literal so store them in respective tables
| Symbol | Address |
|---|---|
| X | – – – |
| L1 | 202 |
| Literal | Address |
|---|---|
| =’3′ | – – – |
| =’2′ | – – – |
Step-5: LTORG 203
Assign address to first literal specified by LC value, i.e., 203
| Literal | Address |
|---|---|
| =’3′ | 203 |
| =’2′ | – – – |
Step-6: X DS 1 204
It is a data declaration statement i.e X is assigned data space of 1. But X is a symbol which was referred earlier in step 3 and defined in step 6.This condition is called Forward Reference Problem where variable is referred prior to its declaration and can be solved by back-patching. So now assembler will assign X the address specified by LC value of current step.
| Symbol | Address |
|---|---|
| X | 204 |
| L1 | 202 |
Step-7: END 205
Program finishes execution and remaining literal will get address specified by LC value of END instruction. Here is the complete symbol and literal table made by pass 1 of assembler.
| Symbol | Address |
|---|---|
| X | 204 |
| L1 | 202 |
| Literal | Address |
|---|---|
| =’3′ | 203 |
| =’2′ | 205 |
Now tables generated by pass 1 along with their LC value will go to pass-2 of assembler for further processing of pseudo-opcodes and machine op-codes.
Working of Pass-2:
Pass-2 of assembler generates machine code by converting symbolic machine-opcodes into their respective bit configuration(machine understandable form). It stores all machine-opcodes in MOT table (op-code table) with symbolic code, their length and their bit configuration. It will also process pseudo-ops and will store them in POT table(pseudo-op table).
How does an assembler work?
I am looking for a brief description of the use of an assembler in producing machine code.
So I know that assembly is a 1:1 translation of machine code. But I am getting confused about object code and linkers and how they place into it.
I don’t need a complex answer just a simple one will do fine
2 Answers 2
Trending sort
Trending sort is based off of the default sorting method — by highest score — but it boosts votes that have happened recently, helping to surface more up-to-date answers.
It falls back to sorting by highest score if no posts are trending.
Switch to Trending sort
Both an assembler and a compiler translate source files into object files.
Object files are effectively an intermediate step before the final executable output (generated by the linker).
The linker takes the specified object files and libraries (which are packages of object files) and resolves relocation (or ‘fixup’) records.
These relocation records are made when the compiler/assembler doesn’t know the address of a function or variable used in the source code, and generates a reference for it by name, which can be resolved by the linker.
But, a relocation record is made for the 4 bytes of the address :
The offset is ‘1’ and the type is ‘R_X86_64_PC32’ which tells the linker to resolve this reference, and put the resolved address into the specified offset.
When and how to use an assembler. Assembly programming basics
The basics of programming in assembly, the design of the processor, registers, memory, instruction, and use of assembly language within C++ and Delphi.
1. Introduction to assembly
Assembly language, a low-level programming language which allows you to use all the features of a computer processor is nowadays somewhat forgotten by “modern” developers.
The main reason for this is that writing in assembly is not the simplest of tasks, and is very time-consuming (testing code, finding bugs etc.).
However, in some situations assembly may be an ideal solution. An example is any kind of algorithm where speed is essential, such as in cryptographic (i.e. encryption) algorithms.
Despite incredible advancements in compilers in recent years, algorithms such as Blowfish, Rijndael, Idea written in assembly and “manually” optimised show significant speed advantages over their counterparts written e.g. in C++ and compiled at the maximum optimisation level.
In addition to cryptography, assembly is also often used by game developers. The best example may be the game QUAKE 2. After the publication of its source code, it turned out that all the algorithms that require speed were written in assembly.
So let’s get started. To be clear, I should add that in this article I will focus on assembly for x86 processors, and its use in a Windows environment.
2. Fundamentals of assembly
If you have never written in assembly, before you can even create the simplest program, you must first learn several fundamentals like the CPU registers, instructions, and the stack.
From the programmer’s perspective, a standard processor (I will use the Intel Pentium MMX as an example, as it is all I’ve got 🙂 has a large range of instructions ranging from 8 to 16 to 32-bit x86 instructions, as well as floating point and MMX instructions.
2.1. CPU registers
| Register Name | 16-bit half | 8-bit halves | Description |
|---|---|---|---|
| EAX | AX | AH and AL | Accumulator |
| EBX | BX | BH and BL | Base |
| ECX | CX | CH and CL | Counter for string operations and loops |
| EDX | DX | DH and DL | Data |
| ESI | SI | n/a | Source register for string instructions |
| EDI | DI | n/a | Destination register for string instructions |
| EBP | BP | n/a | Pointer to data within the stack, used by functions to locate parameters saved on the stack |
| ESP | SP | n/a | Stack pointer |
2.2. General purpose registers
When writing a program, or inline assembly code under Windows, you can use all the general purpose registers, but using the special registers ESP and EBP can interfere with the operation of the program. For example, if you reset the ESP register to zero within a function, the program will most likely crash later (e.g. if the program tries to return from the function).
2.3. The stack
The stack is an area of memory reserved for the needs of the program. These include passing parameters to functions (as 32-bit values), temporary data storage, and all local variables. When the program starts, the ESP register (stack pointer) points to the end of the stack. When data is stored on the stack, the ESP register is decremented, and the data is then stored in the memory location which ESP points to. To store data on the stack, the push instruction is used, for instance:
2.4. Limitations in Windows
If you have written assembly programs under MS/DOS, where there were no limitations, you will need to be aware that there are some differences under Windows. As I said earlier, in assembly we can use all the instructions that the CPU supports, however some instructions are not permitted by the operating system, in our case Windows. For instance, if we use I/O port instructions, the compiler will not give an error, but the program will most likely crash if these instructions are executed under Windows.
Instructions which can cause the program to be terminated include the above-mentioned I/O port instructions, as well as instructions that refer to interrupts, segment registers and control registers.
3. Using assembly language
To take advantage of the benefits of assembly, you must first check whether your development tools allow its use. Products such as Borland Delphi, Builder, Watcom C++ or Microsoft Visual C++ allow you to use (compile) assembly code; Visual Basic is the only popular RAD package which does not allow writing code in assembly. These products support the use of assembly code in two ways. The first is called inline assembly, where the assembly code is inserted into the regular code written in e.g. C++. The second method is linking modules (i.e. separate files) written in assembly with modules written e.g. in Delphi or C++.
3.1. Inline assembly
Before you start writing assembly code, you must check how to write it, because there are two types of syntax for assembly code. The first type is called “intel syntax”, and is used in products such as Delphi, Builder, MSVC, Borland TASM, Microsoft MASM (assembly compilers). This syntax is now the standard and is used in 90% of sources. The second type is called “at&t syntax”, and is used e.g. in C compilers, such as GCC (Linux platform), DJGPP and LCC.
Inline assembly is the easiest way to write asm code. When writing assembly code in Delphi or Builder, it must be enclosed between the asm keyword marking the beginning of the assembly code, and the end; keyword after the code. For example:
Writing inline assembly in MSVC only really differs in how the assembly code is introduced to the compiler:
3.2. Using variables in assembly
Writing in assembly, you have access to all global variables, and if the code is in a procedure, it also has access to the local variables and parameters of the procedure/function, so its capabilities are practically the same as normal code. An example of the use of global and local variables:
The example for MSVC is not much different from that of Delphi:
You can write entire functions in assembly language. When doing this, there are a few things to keep in mind. If the function returns a value, we must ensure that the returned value is stored in the EAX register before leaving the function. A simple example:
We already know that functions written in assembly must place the return value in the EAX register, but what about the other registers?
When writing code in assembly that uses the stack, special attention should be paid to ensuring that the stack pointer ESP is always restored. E.g. if the procedure or function stores something on the stack, then this item must be removed before exiting the function. This time we’ll look at an example in MSVC:
3.3. Calling functions from assembly
| Name | in C code | Parameters | Return values | Modified registers | Info |
| cdecl | cdecl | passed on the stack; the parameters are not removed by the function | eax, 8 bytes: eax:edx | eax, ecx, edx, st(0), st(7), mm0, mm7, xmm0, xmm7 | This is the method of calling C library functions, introduced by Microsoft. All system functions on the Linux platform also use this convention |
| fastcall | __fastcall | ecx, edx, any remaining parameters are passed on the stack | eax, 8 bytes: eax:edx | eax, ecx, edx, st(0), st(7), mm0, mm7, xmm0, xmm7 | Microsoft introduced this standard, but later switched to the cdecl convention in its products |
| watcom | __declspec (wcall) | eax, ebx, ecx, edx | eax, 8 bytes: eax:edx | eax | This function calling convention was introduced by Watcom in their C++ compiler |
| stdcall | __stdcall | passed on the stack; parameters are removed by the function | eax, 8 bytes: eax:edx | eax, ecx, edx, st(0), st(7), mm0, mm7, xmm0, xmm7 | The default calling convention for Windows API functions in DLLs |
| register | n/a | eax, edx, ecx, any remaining parameters are passed on the stack | eax | eax, ecx, edx, st(0), st(7), mm0, mm7, xmm0, xmm7 | This is the calling convention used in Borland’s Delphi |
The correct calling convention for functions in our own programs (as opposed to WinApi) often depends on the options with which the program was compiled. In Delphi the default convention is “register”, while for most programs written in C, the default is “cdecl”.
WinApi functions (Windows system functions) use the mechanism stdcall, where function parameters are first stored on the stack, and then the function is called. After the function returns, there is no need to adjust the stack (remove the previously saved parameters), since the called function does it for us. Interestingly, a few WinApi functions do not use the stdcall convention, but instead use cdecl, that is, the parameters are stored on the stack, then the function is called, but afterwards the stack must be cleaned up manually. An example of such a function is the wsprintfA function from the Windows system library user32.dll (whose counterpart in the C standard library is sprintf ). The cdecl was probably chosen because these functions do not have a fixed number of parameters:
4. MMX instructions
MMX is the name of an extension to the Pentium series of processors, introduced by Intel. The name is said to be an abbreviation of “MultiMedia eXtensions”, but Intel denies this, and has never explained the issue. The MMX extension to the Pentium line of processors includes a set of new instructions (57, to be exact), and 8 additional 64-bit registers.
MMX registers are shared with the FPU registers. This means that you cannot mix FPU (Floating Point Unit) instructions with MMX unit instructions otherwise the contents of the registers will be corrupted. MMX instructions can operate on data in SIMD fashion (Single Instruction Multiple Data). This means that one operation can be performed simultaneously on many data items, which is not possible using standard x86 instruction.
MMX instructions are ideal for processing multimedia data, e.g. video, graphics, sound. For example, programs such as DivX or Winamp make intensive use of MMX code. Currently, most processors produced by Intel, AMD and Cyrix possess MMX support.
Although MMX has for quite a few years been practically standard, HLL compilers generally do not generate MMX code (except specialised compilers like VectorC). It seems that the natural solution is to program MMX in assembly.
Writing procedures using MMX can sometimes get a 100% speed increase compared to the original code. This is possible because of the aforementioned SIMD mode. Imagine a situation where we have two tables of 8 bytes, and we want to add corresponding bytes from both tables to each other. In C++ we would do it this way:
There’s no problem with this, but the operation of adding bytes will be repeated 8 times. Let’s look at how this can be done much more efficiently by using MMX:
In total, just one instruction is executed instead of 8 additions. Neat, isn’t it? And more importantly, efficient. Here a few examples of graphical functions:
5. When to use assembly
As I mentioned at the beginning of the article, assembly is used mainly where speed is important. When writing an algorithm, we should sometimes stop and ask ourselves whether our program could be enhanced, if at some critical points (for instance in loops, etc.), we were to employ, say, MMX.
Imagine that you just wrote an mp3 encoder, and a competitor did the same, but you used hand-written MMX code which is three times faster than the competition. Which product will users choose, when they can complete a task in 10 minutes instead of 30? The answer is obvious.
Besides being ideal for writing algorithms that require speed, assembly is also used to write particular programs such as EXE-compressors. I’ll bet that most people will think of programs like UPX or Aspack, which are used to compress executables. Put simply, if you write a program which occupies let’s say 700 kB, when compressed by UPX its size will decrease to approx. 300 kB, but the program will still be in the form of an EXE file, and will be just as functional as before compression. This is achieved by using assembly to write a loader for the code. This is a fragment of code that is stored in the EXE file (almost like a virus), and when you start such a program, the loader decompresses the remainder of the EXE file and allows it to run. Writing a loader in a HLL, whether it be C++, Delphi or even Power Basic is virtually impossible.
It can be said that assembly programming is only useful for speed and unusual applications, but this is not entirely true. Writing in assembly language can be more than just inline routines and a few procedures here and there. Entire programs can be written in assembly language! Sometimes I hear people say that it is impossible; that you can’t write large applications in assembly from scratch. Often these are people who have only dabbled in assembly for a few hours. If you are a competent programmer, there is nothing stopping you from building professional applications in assembly language. Writing programs in assembly gives us full control over them. Everything is up to us, the program is executed according to our will, and we are not at the mercy of the compiler.
These days, writing in assembly is reasonably simple and convenient. A lot of people around the world are beginning to see the magic of this language. People are creating many projects; you can find a whole bunch of sample tutorials and source code, thanks to which many challenges have ceased to be problems. Writing entire applications in assembly also has the advantage that a project with 5MB of source code will be compiled to an executable of approximately 90kB. Compare an application written in Delphi 6, containing 1 window, which takes approx. 300kb compiled, to a program written in assembly language which does exactly the same thing, and works on every Windows release from 95 to XP, with just a 4kb executable. Why the big difference? It’s simple: the compiler adds a lot of unnecessary things, “just in case”. Why isn’t this made more efficient? We should ask the companies who make compilers.
Despite the fact that assembly can be used for many useful things, it is also used to write malicious programs, such as viruses, ransomware, or exploits, but in the words of Winnie the Pooh, that is a story for another day.
6. Summary
These examples represent only a small range of what is possible with assembly. There is a lot to discover, just as much for me as there is for you, because contrary to what they say, assembly is not dead, it is constantly changing, evolving, giving us possibilities which do not exist in any high-level language. The terms we hear in the press: SSE, SSE2, 3DNow, are not fiction. Everything is out there. We just have to reach for it.
For my part, writing assembly language gives me a feeling of freedom, which I never found when writing in any other language. I hope that your journey into assembly doesn’t end with this article!
7. References
| a page for assembly programmers, sources, tutorials, forums | |
| www.int80h.org | FreeBSA assembly programming |
| programming Windows graphics, algorithms, fractals | |
| Chris Dragan’s page, many samples in assembler (MMX) | |
| www.azillionmonkeys.com/qed/index.html | an excellent articles about low level code optimization (MMX, Pentium) |
| Assembly Programming Journal, a computer programming magazine for the assembler language, C libraries code optimization, assembly programming for Unix shells, game programming in assembly with DirectX and many other interesting resources | |
| www.nasm.us | an official page for the free NASM assembler framework (Windows, Unix) |
| www.borland.com/Products/Software-Testing/Automated-Testing/Devpartner-Studio | SoftIce, debugger that let you analyze any application on high and low level formats |
About the Author
Bartosz Wójcik — is an author of PELock software protection and licensing system for programmers.
What is Assembly Language?
By 
Introduction to Assembly Language
Assembly Language is a low-level programming language. It helps in understanding the programming language to machine code. In computers, there is an assembler that helps in converting the assembly code into machine code executable. Assembly language is designed to understand the instruction and provide it to machine language for further processing. It mainly depends on the architecture of the system, whether it is the operating system or computer architecture.
Assembly Language mainly consists of mnemonic processor instructions or data and other statements or instructions. It is produced with the help of compiling the high-level language source code like C, C++. Assembly Language helps in fine-tuning the program.
Web development, programming languages, Software testing & others
Why is Assembly Language Useful?
Assembly language helps programmers to write human-readable code that is almost similar to machine language. Machine language is difficult to understand and read as it is just a series of numbers. Assembly language helps in providing full control of what tasks a computer is performing.
Example:
Find the below steps to print “Hello world” in Windows
Why should you learn Assembly Language?
The learning of assembly language is still important for programmers. It helps in taking complete control over the system and its resources. By learning assembly language, the programmer can write the code to access registers and retrieve the memory address of pointers and values. It mainly helps in speed optimization that increases efficiency and performance.
Assembly language learning helps in understanding the processor and memory functions. If the programmer is writing any program that needs to be a compiler, that means the programmer should have a complete understanding of the processor. Assembly language helps in understanding the work of processors and memory. It is cryptic and symbolic language.
Assembly Language helps in contacting the hardware directly. This language is mainly based on computer architecture, and it recognizes a certain type of processor and its different for different CPUs. Assembly language refers to transparency compared to other high-level languages. It has a small number of operations, but it is helpful in understanding the algorithms and other flow of controls. It makes the code less complex and easy debugging as well.
Features
The features of the assembly language are mentioned below:
Assemblers
The assemblers are used to translate the assembly language into machine language. There are two types of assembler are:
Advantages and Disadvantages
Mentioned are some advantages and disadvantages:
Advantages
Below are the advantages:
Disadvantages
Below mentioned are the disadvantages:
Conclusion
Assembly language is very important for understanding the computer architecture and programs for the programmers. The programmers mainly used many other programming languages for application development and software, but assembly language is also important. It helps programmers to achieve a lot if they implement the assembly language. Assemblies contain a lot of metadata that is version number, localization details, and other product details. It is an important part and provided to the user after digitally signed.
If an individual wants to know how the system works and the processor as well, then assembly language is the one that solves the purpose. It helps in all aspects, from understanding the algorithm of the program to the processor working and registering the registers of the computer. It depends on individual choice with which language to continue.
Recommended Article
This has been a guide to What is Assembly Language. Here we have discuss the Features, Advantages, and Disadvantages of Assembly Language. You can also go through our other suggested articles to learn more –
All in One Software Development Bundle (600+ Courses, 50+ projects)
What is Assembly Language?
Each personal computer has a microprocessor that manages the computer’s arithmetical, logical, and control activities.
Each family of processors has its own set of instructions for handling various operations such as getting input from keyboard, displaying information on screen and performing various other jobs. These set of instructions are called ‘machine language instructions’.
A processor understands only machine language instructions, which are strings of 1’s and 0’s. However, machine language is too obscure and complex for using in software development. So, the low-level assembly language is designed for a specific family of processors that represents various instructions in symbolic code and a more understandable form.
Advantages of Assembly Language
Having an understanding of assembly language makes one aware of −
Other advantages of using assembly language are −
It requires less memory and execution time;
It allows hardware-specific complex jobs in an easier way;
It is suitable for time-critical jobs;
It is most suitable for writing interrupt service routines and other memory resident programs.
Basic Features of PC Hardware
The main internal hardware of a PC consists of processor, memory, and registers. Registers are processor components that hold data and address. To execute a program, the system copies it from the external device into the internal memory. The processor executes the program instructions.
The fundamental unit of computer storage is a bit; it could be ON (1) or OFF (0) and a group of 8 related bits makes a byte on most of the modern computers.
So, the parity bit is used to make the number of bits in a byte odd. If the parity is even, the system assumes that there had been a parity error (though rare), which might have been caused due to hardware fault or electrical disturbance.
The processor supports the following data sizes −
Binary Number System
Every number system uses positional notation, i.e., each position in which a digit is written has a different positional value. Each position is power of the base, which is 2 for binary number system, and these powers begin at 0 and increase by 1.
The following table shows the positional values for an 8-bit binary number, where all bits are set ON.
| Bit value | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 |
|---|---|---|---|---|---|---|---|---|
| Position value as a power of base 2 | 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
| Bit number | 7 | 6 | 5 | 4 | 3 | 2 | 1 | 0 |
The value of a binary number is based on the presence of 1 bits and their positional value. So, the value of a given binary number is −
1 + 2 + 4 + 8 +16 + 32 + 64 + 128 = 255
Hexadecimal Number System
Hexadecimal number system uses base 16. The digits in this system range from 0 to 15. By convention, the letters A through F is used to represent the hexadecimal digits corresponding to decimal values 10 through 15.
Hexadecimal numbers in computing is used for abbreviating lengthy binary representations. Basically, hexadecimal number system represents a binary data by dividing each byte in half and expressing the value of each half-byte. The following table provides the decimal, binary, and hexadecimal equivalents −
| Decimal number | Binary representation | Hexadecimal representation |
|---|---|---|
| 0 | 0 | 0 |
| 1 | 1 | 1 |
| 2 | 10 | 2 |
| 3 | 11 | 3 |
| 4 | 100 | 4 |
| 5 | 101 | 5 |
| 6 | 110 | 6 |
| 7 | 111 | 7 |
| 8 | 1000 | 8 |
| 9 | 1001 | 9 |
| 10 | 1010 | A |
| 11 | 1011 | B |
| 12 | 1100 | C |
| 13 | 1101 | D |
| 14 | 1110 | E |
| 15 | 1111 | F |
To convert a binary number to its hexadecimal equivalent, break it into groups of 4 consecutive groups each, starting from the right, and write those groups over the corresponding digits of the hexadecimal number.
To convert a hexadecimal number to binary, just write each hexadecimal digit into its 4-digit binary equivalent.
Binary Arithmetic
The following table illustrates four simple rules for binary addition −
| (i) | (ii) | (iii) | (iv) |
|---|---|---|---|
| 1 | |||
| 0 | 1 | 1 | 1 |
| +0 | +0 | +1 | +1 |
| =0 | =1 | =10 | =11 |
Rules (iii) and (iv) show a carry of a 1-bit into the next left position.
| Decimal | Binary |
|---|---|
| 60 | 00111100 |
| +42 | 00101010 |
| 102 | 01100110 |
A negative binary value is expressed in two’s complement notation. According to this rule, to convert a binary number to its negative value is to reverse its bit values and add 1.
To subtract one value from another, convert the number being subtracted to two’s complement format and add the numbers.
Subtract 42 from 53
Overflow of the last 1 bit is lost.
Addressing Data in Memory
The process through which the processor controls the execution of instructions is referred as the fetch-decode-execute cycle or the execution cycle. It consists of three continuous steps −
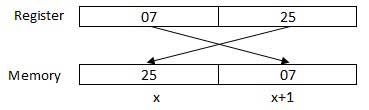
The processor may access one or more bytes of memory at a time. Let us consider a hexadecimal number 0725H. This number will require two bytes of memory. The high-order byte or most significant byte is 07 and the low-order byte is 25.
The processor stores data in reverse-byte sequence, i.e., a low-order byte is stored in a low memory address and a high-order byte in high memory address. So, if the processor brings the value 0725H from register to memory, it will transfer 25 first to the lower memory address and 07 to the next memory address.
x: memory address
When the processor gets the numeric data from memory to register, it again reverses the bytes. There are two kinds of memory addresses −
Local Environment Setup
Assembly language is dependent upon the instruction set and the architecture of the processor. In this tutorial, we focus on Intel-32 processors like Pentium. To follow this tutorial, you will need −
There are many good assembler programs, such as −
We will use the NASM assembler, as it is −
Installing NASM
If you select «Development Tools» while installing Linux, you may get NASM installed along with the Linux operating system and you do not need to download and install it separately. For checking whether you already have NASM installed, take the following steps −
Open a Linux terminal.
Type whereis nasm and press ENTER.
If it is already installed, then a line like, nasm: /usr/bin/nasm appears. Otherwise, you will see just nasm:, then you need to install NASM.
To install NASM, take the following steps −
Check The netwide assembler (NASM) website for the latest version.
cd to nasm-X.XX and type ./configure. This shell script will find the best C compiler to use and set up Makefiles accordingly.
Type make to build the nasm and ndisasm binaries.
Type make install to install nasm and ndisasm in /usr/local/bin and to install the man pages.
This should install NASM on your system. Alternatively, you can use an RPM distribution for the Fedora Linux. This version is simpler to install, just double-click the RPM file.
An assembly program can be divided into three sections −
The data section,
The bss section, and
The text section.
The data Section
The data section is used for declaring initialized data or constants. This data does not change at runtime. You can declare various constant values, file names, or buffer size, etc., in this section.
The syntax for declaring data section is −
The bss Section
The bss section is used for declaring variables. The syntax for declaring bss section is −
The text section
The text section is used for keeping the actual code. This section must begin with the declaration global _start, which tells the kernel where the program execution begins.
The syntax for declaring text section is −
Comments
Assembly language comment begins with a semicolon (;). It may contain any printable character including blank. It can appear on a line by itself, like −
or, on the same line along with an instruction, like −
Assembly Language Statements
Assembly language programs consist of three types of statements −
The executable instructions or simply instructions tell the processor what to do. Each instruction consists of an operation code (opcode). Each executable instruction generates one machine language instruction.
The assembler directives or pseudo-ops tell the assembler about the various aspects of the assembly process. These are non-executable and do not generate machine language instructions.
Macros are basically a text substitution mechanism.
Syntax of Assembly Language Statements
Assembly language statements are entered one statement per line. Each statement follows the following format −
The fields in the square brackets are optional. A basic instruction has two parts, the first one is the name of the instruction (or the mnemonic), which is to be executed, and the second are the operands or the parameters of the command.
Following are some examples of typical assembly language statements −
The Hello World Program in Assembly
The following assembly language code displays the string ‘Hello World’ on the screen −
When the above code is compiled and executed, it produces the following result −
Compiling and Linking an Assembly Program in NASM
Make sure you have set the path of nasm and ld binaries in your PATH environment variable. Now, take the following steps for compiling and linking the above program −
Type the above code using a text editor and save it as hello.asm.
Make sure that you are in the same directory as where you saved hello.asm.
If there is any error, you will be prompted about that at this stage. Otherwise, an object file of your program named hello.o will be created.
Execute the program by typing ./hello
If you have done everything correctly, it will display ‘Hello, world!’ on the screen.
We have already discussed the three sections of an assembly program. These sections represent various memory segments as well.
Interestingly, if you replace the section keyword with segment, you will get the same result. Try the following code −
When the above code is compiled and executed, it produces the following result −
Memory Segments
A segmented memory model divides the system memory into groups of independent segments referenced by pointers located in the segment registers. Each segment is used to contain a specific type of data. One segment is used to contain instruction codes, another segment stores the data elements, and a third segment keeps the program stack.
In the light of the above discussion, we can specify various memory segments as −
Code segment − It is represented by .text section. This defines an area in memory that stores the instruction codes. This is also a fixed area.
Stack − This segment contains data values passed to functions and procedures within the program.
Processor operations mostly involve processing data. This data can be stored in memory and accessed from thereon. However, reading data from and storing data into memory slows down the processor, as it involves complicated processes of sending the data request across the control bus and into the memory storage unit and getting the data through the same channel.
To speed up the processor operations, the processor includes some internal memory storage locations, called registers.
The registers store data elements for processing without having to access the memory. A limited number of registers are built into the processor chip.
Processor Registers
There are ten 32-bit and six 16-bit processor registers in IA-32 architecture. The registers are grouped into three categories −
The general registers are further divided into the following groups −
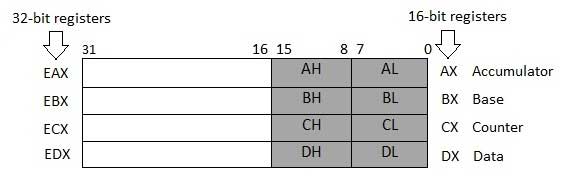
Data Registers
Four 32-bit data registers are used for arithmetic, logical, and other operations. These 32-bit registers can be used in three ways −
As complete 32-bit data registers: EAX, EBX, ECX, EDX.
Lower halves of the 32-bit registers can be used as four 16-bit data registers: AX, BX, CX and DX.
Lower and higher halves of the above-mentioned four 16-bit registers can be used as eight 8-bit data registers: AH, AL, BH, BL, CH, CL, DH, and DL.
Some of these data registers have specific use in arithmetical operations.
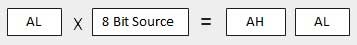
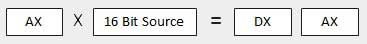
AX is the primary accumulator; it is used in input/output and most arithmetic instructions. For example, in multiplication operation, one operand is stored in EAX or AX or AL register according to the size of the operand.
BX is known as the base register, as it could be used in indexed addressing.
CX is known as the count register, as the ECX, CX registers store the loop count in iterative operations.
DX is known as the data register. It is also used in input/output operations. It is also used with AX register along with DX for multiply and divide operations involving large values.
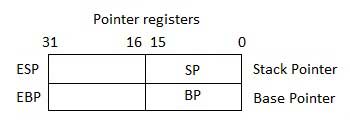
Pointer Registers
The pointer registers are 32-bit EIP, ESP, and EBP registers and corresponding 16-bit right portions IP, SP, and BP. There are three categories of pointer registers −
Instruction Pointer (IP) − The 16-bit IP register stores the offset address of the next instruction to be executed. IP in association with the CS register (as CS:IP) gives the complete address of the current instruction in the code segment.
Stack Pointer (SP) − The 16-bit SP register provides the offset value within the program stack. SP in association with the SS register (SS:SP) refers to be current position of data or address within the program stack.
Base Pointer (BP) − The 16-bit BP register mainly helps in referencing the parameter variables passed to a subroutine. The address in SS register is combined with the offset in BP to get the location of the parameter. BP can also be combined with DI and SI as base register for special addressing.
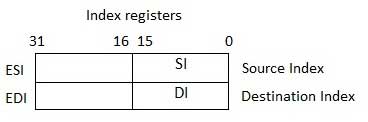
Index Registers
The 32-bit index registers, ESI and EDI, and their 16-bit rightmost portions. SI and DI, are used for indexed addressing and sometimes used in addition and subtraction. There are two sets of index pointers −
Source Index (SI) − It is used as source index for string operations.
Destination Index (DI) − It is used as destination index for string operations.
Control Registers
The 32-bit instruction pointer register and the 32-bit flags register combined are considered as the control registers.
Many instructions involve comparisons and mathematical calculations and change the status of the flags and some other conditional instructions test the value of these status flags to take the control flow to other location.
The common flag bits are:
Overflow Flag (OF) − It indicates the overflow of a high-order bit (leftmost bit) of data after a signed arithmetic operation.
Direction Flag (DF) − It determines left or right direction for moving or comparing string data. When the DF value is 0, the string operation takes left-to-right direction and when the value is set to 1, the string operation takes right-to-left direction.
Interrupt Flag (IF) − It determines whether the external interrupts like keyboard entry, etc., are to be ignored or processed. It disables the external interrupt when the value is 0 and enables interrupts when set to 1.
Trap Flag (TF) − It allows setting the operation of the processor in single-step mode. The DEBUG program we used sets the trap flag, so we could step through the execution one instruction at a time.
Sign Flag (SF) − It shows the sign of the result of an arithmetic operation. This flag is set according to the sign of a data item following the arithmetic operation. The sign is indicated by the high-order of leftmost bit. A positive result clears the value of SF to 0 and negative result sets it to 1.
Zero Flag (ZF) − It indicates the result of an arithmetic or comparison operation. A nonzero result clears the zero flag to 0, and a zero result sets it to 1.
Auxiliary Carry Flag (AF) − It contains the carry from bit 3 to bit 4 following an arithmetic operation; used for specialized arithmetic. The AF is set when a 1-byte arithmetic operation causes a carry from bit 3 into bit 4.
Parity Flag (PF) − It indicates the total number of 1-bits in the result obtained from an arithmetic operation. An even number of 1-bits clears the parity flag to 0 and an odd number of 1-bits sets the parity flag to 1.
Carry Flag (CF) − It contains the carry of 0 or 1 from a high-order bit (leftmost) after an arithmetic operation. It also stores the contents of last bit of a shift or rotate operation.
The following table indicates the position of flag bits in the 16-bit Flags register:
| Flag: | O | D | I | T | S | Z | A | P | C | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Bit no: | 15 | 14 | 13 | 12 | 11 | 10 | 9 | 8 | 7 | 6 | 5 | 4 | 3 | 2 | 1 | 0 |
Segment Registers
Segments are specific areas defined in a program for containing data, code and stack. There are three main segments −
Code Segment − It contains all the instructions to be executed. A 16-bit Code Segment register or CS register stores the starting address of the code segment.
Data Segment − It contains data, constants and work areas. A 16-bit Data Segment register or DS register stores the starting address of the data segment.
Stack Segment − It contains data and return addresses of procedures or subroutines. It is implemented as a ‘stack’ data structure. The Stack Segment register or SS register stores the starting address of the stack.
In assembly programming, a program needs to access the memory locations. All memory locations within a segment are relative to the starting address of the segment. A segment begins in an address evenly divisible by 16 or hexadecimal 10. So, the rightmost hex digit in all such memory addresses is 0, which is not generally stored in the segment registers.
The segment registers stores the starting addresses of a segment. To get the exact location of data or instruction within a segment, an offset value (or displacement) is required. To reference any memory location in a segment, the processor combines the segment address in the segment register with the offset value of the location.
Example
Look at the following simple program to understand the use of registers in assembly programming. This program displays 9 stars on the screen along with a simple message −
When the above code is compiled and executed, it produces the following result −
System calls are APIs for the interface between the user space and the kernel space. We have already used the system calls. sys_write and sys_exit, for writing into the screen and exiting from the program, respectively.
Linux System Calls
You can make use of Linux system calls in your assembly programs. You need to take the following steps for using Linux system calls in your program −
There are six registers that store the arguments of the system call used. These are the EBX, ECX, EDX, ESI, EDI, and EBP. These registers take the consecutive arguments, starting with the EBX register. If there are more than six arguments, then the memory location of the first argument is stored in the EBX register.
The following code snippet shows the use of the system call sys_exit −
The following code snippet shows the use of the system call sys_write −
All the syscalls are listed in /usr/include/asm/unistd.h, together with their numbers (the value to put in EAX before you call int 80h).
The following table shows some of the system calls used in this tutorial −
| %eax | Name | %ebx | %ecx | %edx | %esx | %edi |
|---|---|---|---|---|---|---|
| 1 | sys_exit | int | — | — | — | — |
| 2 | sys_fork | struct pt_regs | — | — | — | — |
| 3 | sys_read | unsigned int | char * | size_t | — | — |
| 4 | sys_write | unsigned int | const char * | size_t | — | — |
| 5 | sys_open | const char * | int | int | — | — |
| 6 | sys_close | unsigned int | — | — | — | — |
Example
The following example reads a number from the keyboard and displays it on the screen −
When the above code is compiled and executed, it produces the following result −
Most assembly language instructions require operands to be processed. An operand address provides the location, where the data to be processed is stored. Some instructions do not require an operand, whereas some other instructions may require one, two, or three operands.
When an instruction requires two operands, the first operand is generally the destination, which contains data in a register or memory location and the second operand is the source. Source contains either the data to be delivered (immediate addressing) or the address (in register or memory) of the data. Generally, the source data remains unaltered after the operation.
The three basic modes of addressing are −
Register Addressing
In this addressing mode, a register contains the operand. Depending upon the instruction, the register may be the first operand, the second operand or both.
As processing data between registers does not involve memory, it provides fastest processing of data.
Immediate Addressing
An immediate operand has a constant value or an expression. When an instruction with two operands uses immediate addressing, the first operand may be a register or memory location, and the second operand is an immediate constant. The first operand defines the length of the data.
Direct Memory Addressing
When operands are specified in memory addressing mode, direct access to main memory, usually to the data segment, is required. This way of addressing results in slower processing of data. To locate the exact location of data in memory, we need the segment start address, which is typically found in the DS register and an offset value. This offset value is also called effective address.
In direct addressing mode, the offset value is specified directly as part of the instruction, usually indicated by the variable name. The assembler calculates the offset value and maintains a symbol table, which stores the offset values of all the variables used in the program.
In direct memory addressing, one of the operands refers to a memory location and the other operand references a register.
Direct-Offset Addressing
This addressing mode uses the arithmetic operators to modify an address. For example, look at the following definitions that define tables of data −
The following operations access data from the tables in the memory into registers −
Indirect Memory Addressing
This addressing mode utilizes the computer’s ability of Segment:Offset addressing. Generally, the base registers EBX, EBP (or BX, BP) and the index registers (DI, SI), coded within square brackets for memory references, are used for this purpose.
Indirect addressing is generally used for variables containing several elements like, arrays. Starting address of the array is stored in, say, the EBX register.
The following code snippet shows how to access different elements of the variable.
The MOV Instruction
We have already used the MOV instruction that is used for moving data from one storage space to another. The MOV instruction takes two operands.
Syntax
The syntax of the MOV instruction is −
The MOV instruction may have one of the following five forms −
Please note that −
The MOV instruction causes ambiguity at times. For example, look at the statements −
It is not clear whether you want to move a byte equivalent or word equivalent of the number 110. In such cases, it is wise to use a type specifier.
Following table shows some of the common type specifiers −
| Type Specifier | Bytes addressed |
|---|---|
| BYTE | 1 |
| WORD | 2 |
| DWORD | 4 |
| QWORD | 8 |
| TBYTE | 10 |
Example
The following program illustrates some of the concepts discussed above. It stores a name ‘Zara Ali’ in the data section of the memory, then changes its value to another name ‘Nuha Ali’ programmatically and displays both the names.
When the above code is compiled and executed, it produces the following result −
NASM provides various define directives for reserving storage space for variables. The define assembler directive is used for allocation of storage space. It can be used to reserve as well as initialize one or more bytes.
Allocating Storage Space for Initialized Data
The syntax for storage allocation statement for initialized data is −
Where, variable-name is the identifier for each storage space. The assembler associates an offset value for each variable name defined in the data segment.
There are five basic forms of the define directive −
| Directive | Purpose | Storage Space |
|---|---|---|
| DB | Define Byte | allocates 1 byte |
| DW | Define Word | allocates 2 bytes |
| DD | Define Doubleword | allocates 4 bytes |
| DQ | Define Quadword | allocates 8 bytes |
| DT | Define Ten Bytes | allocates 10 bytes |
Following are some examples of using define directives −
Please note that −
Each byte of character is stored as its ASCII value in hexadecimal.
Each decimal value is automatically converted to its 16-bit binary equivalent and stored as a hexadecimal number.
Processor uses the little-endian byte ordering.
Negative numbers are converted to its 2’s complement representation.
Short and long floating-point numbers are represented using 32 or 64 bits, respectively.
The following program shows the use of define directive −
When the above code is compiled and executed, it produces the following result −
Allocating Storage Space for Uninitialized Data
The reserve directives are used for reserving space for uninitialized data. The reserve directives take a single operand that specifies the number of units of space to be reserved. Each define directive has a related reserve directive.
There are five basic forms of the reserve directive −
| Directive | Purpose |
|---|---|
| RESB | Reserve a Byte |
| RESW | Reserve a Word |
| RESD | Reserve a Doubleword |
| RESQ | Reserve a Quadword |
| REST | Reserve a Ten Bytes |
Multiple Definitions
You can have multiple data definition statements in a program. For example −
The assembler allocates contiguous memory for multiple variable definitions.
Multiple Initializations
The TIMES directive allows multiple initializations to the same value. For example, an array named marks of size 9 can be defined and initialized to zero using the following statement −
The TIMES directive is useful in defining arrays and tables. The following program displays 9 asterisks on the screen −
When the above code is compiled and executed, it produces the following result −
There are several directives provided by NASM that define constants. We have already used the EQU directive in previous chapters. We will particularly discuss three directives −
The EQU Directive
The EQU directive is used for defining constants. The syntax of the EQU directive is as follows −
You can then use this constant value in your code, like −
The operand of an EQU statement can be an expression −
Above code segment would define AREA as 200.
Example
The following example illustrates the use of the EQU directive −
When the above code is compiled and executed, it produces the following result −
The %assign Directive
The %assign directive can be used to define numeric constants like the EQU directive. This directive allows redefinition. For example, you may define the constant TOTAL as −
Later in the code, you can redefine it as −
This directive is case-sensitive.
The %define Directive
The %define directive allows defining both numeric and string constants. This directive is similar to the #define in C. For example, you may define the constant PTR as −
The above code replaces PTR by [EBP+4].
This directive also allows redefinition and it is case-sensitive.
The INC Instruction
The INC instruction is used for incrementing an operand by one. It works on a single operand that can be either in a register or in memory.
Syntax
The INC instruction has the following syntax −
The operand destination could be an 8-bit, 16-bit or 32-bit operand.
Example
The DEC Instruction
The DEC instruction is used for decrementing an operand by one. It works on a single operand that can be either in a register or in memory.
Syntax
The DEC instruction has the following syntax −
The operand destination could be an 8-bit, 16-bit or 32-bit operand.
Example
The ADD and SUB Instructions
The ADD and SUB instructions are used for performing simple addition/subtraction of binary data in byte, word and doubleword size, i.e., for adding or subtracting 8-bit, 16-bit or 32-bit operands, respectively.
Syntax
The ADD and SUB instructions have the following syntax −
The ADD/SUB instruction can take place between −
However, like other instructions, memory-to-memory operations are not possible using ADD/SUB instructions. An ADD or SUB operation sets or clears the overflow and carry flags.
Example
The following example will ask two digits from the user, store the digits in the EAX and EBX register, respectively, add the values, store the result in a memory location ‘res‘ and finally display the result.
When the above code is compiled and executed, it produces the following result −
The program with hardcoded variables −
When the above code is compiled and executed, it produces the following result −
The MUL/IMUL Instruction
There are two instructions for multiplying binary data. The MUL (Multiply) instruction handles unsigned data and the IMUL (Integer Multiply) handles signed data. Both instructions affect the Carry and Overflow flag.
Syntax
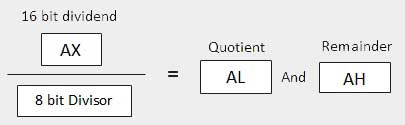
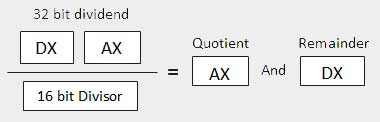
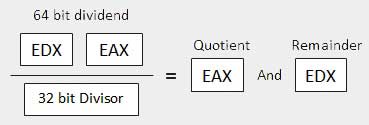
The syntax for the MUL/IMUL instructions is as follows −
Multiplicand in both cases will be in an accumulator, depending upon the size of the multiplicand and the multiplier and the generated product is also stored in two registers depending upon the size of the operands. Following section explains MUL instructions with three different cases −