What on earth made you put that in the threads field loic
What on earth made you put that in the threads field loic
NewEraCracker/LOIC
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
LOIC is for educational purposes only, intended to help server owners develop a «hacker defense» attitude. This tool comes without any warranty.
You may not use this software for illegal or unethical purposes. This includes activities which give rise to criminal or civil liability.
Under no event shall the licensor be responsible for any activities, or misdeeds, by the licensee.
HOW TO RUN ON WINDOWS
GET THE BINARIES!
HOW TO RUN ON LINUX / MACOSX
Run debug binaries with Mono or Wine. Read the wiki at https://github.com/NewEraCracker/LOIC/wiki/_pages for updated instructions.
HIVEMIND mode will connect your client to an IRC server so it can be controlled remotely. Think of this as a voluntary botnet. Please be aware that your client can potentially be made to do naughty things.
Note: It does NOT allow remote administration of your machine; it just providees control of LOIC itself.
If you want to start up in Hivemind mode, run something such as this:
which will connect to irc://irc.server.adress:6667/loic
You can also specify a port and channel:
which will connect to irc://irc.server.adress:1234/secret
In order to run Hivemind Hidden mode, run something such as this:
which will connect to irc://irc.server.adress:6667/loic without any visible GUI.
CONTROLLING LOIC FROM IRC
As an OP, Admin or Owner, set the channel topic or send a message such as the following:
To start an attack, type:
or append «start» to the END of the topic:
To reset LOIC’s options back to their defaults:
To stop an attack:
and be sure to remove «start» from the END of the topic, if it exists, as well.
Take a look at the source code for more details.
About
LOIC (Low Orbit Ion Cannon) � DOS attacking tool

Low Orbit Ion Cannon (LOIC) is an open source network stress testing and denial-of-service attack application, written in C#. LOIC was initially developed by Praetox Technologies, but was later released into the public domain, and now is hosted on several open source platforms.
The software has inspired the creation of an independent JavaScript version called JS LOIC, as well as LOIC-derived web version called Low Orbit Web Cannon. These enable a DoS from a web browser.
LOIC basically turns your computer’s network connection into a firehose of garbage requests, directed towards a target web server. On its own, one computer rarely generates enough TCP, UDP, or HTTP requests at once to overwhelm a web servergarbage requests can easily ignored while legit requests for web pages are responded to as normal.
But when thousands of users run LOIC at once, the wave of requests become overwhelming, often shutting a web server (or one of its connected machines, like a database server) down completely, or preventing legitimate requests from being answered.
Tutorial :
1. Download the software and execute it. lets describe it with a screenshot! 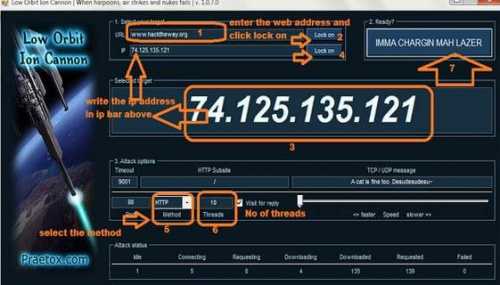
2. Enter the URL which u wanna attack and click on Lock On.
3.The ip address of that very site will get displayed in the “Selected target” caption. Write this ip address in ip bar as shown above and click Lock On.
4. Select the method and number of threads.
5. Click on IMMA CHARGIN MAH LAZER…
Cheers You’re done……….
http://www.mediafire.com/?ctg8c3186mimqx7
we are anonymous
thank you for share.
Fuck that! Just bring it down to backtrack/kali…. Unless you have a mass of attackers using LOIC not much is going to happen and firewalls/tunnels that can filter your attacks. You’re better off building your own attack and actually learning something without using software.
But– Note the speed of a 3G cell phone 😉 if you get the LOIC app for android you can take down a single users pc (I don’t know about a server that’s been put together well and prepared for these attacks though) from approximately 1958 miles within an estimation of 2-4 minutes by yourself. I know this from experience.
Use HTTP for the reasons that the packet size can get pretty hefty and run around 600-750 threads no more using the fastest setting (slider all the way to the left). The app will more than likely crash if you exceed 600-750. When I used it was stable around there but any higher dead. I took a pretty good analysis of these tools too since the whole purpose was to show my friend how to perform a Denial of Service Attack.
Anywho’ I’m going on lol but just saying I’d rather use windows to perform a ddos attack on command shell than LOIC. Just because hacking with GUI requires no skill or knowledge whatsoever! If you want to become a successful hack… Become an information junky don’t half fast it that’s how you get caught. How do you know you can trust someone else’s code and that they aren’t logging in your computer and on their servers, every time you use their software? Think about it….
Not saying LOIC isn’t a clever tool but, it’s kind of obsolete, weak, and noobish….
Here’s pretty much speech of every Denial of Service attack possible @ Defcon ( [deleted user]
9 years ago
Ha ha thanks for the reply and Not saying it’s a bad tool just very obsolete and not much to learn from pushing a couple buttons. lol I mean it serves its purpose of gathering a couple hundred people who hate Scientology together and flooding their networks with data, yeah, but to call yourself a hacker you have to have a little more up your sleeve than just LOIC… cause I mean when your attack fails there’s a million other options but, unless you have a back up plan on what those options are and some knowledge it’s no use. So if you know other types of denial of service attacks then yeah go for it! Serves your purpose as an activist/hacktivist. But hacking usually refers to accessing data/information in unconventional ways. So I don’t get that out of a denial of service of service attack. Plus DOS/DDOS attacks tend to be risky y ‘know. Your ip info is present, information of your system being distributed back and forth, creating somewhat of a connection I guess in a weird way. Just it’s simple to track…. If you want to take down a companies website, play like a ransom. Use your crafty/creative hacker skills to gain access to the server, create a backdoor, make a back up of the the site and databases, once all that good kidnapping stuff is down, lock up all connections to the server (again use crafty hacker skills: crash the server, plant a smart virus, redirect, deface, a back door with a shell running, etc.) and finally delete all of your logs. Security precautions and a plan on how to execute your attack should be done before hand though y ‘know?! So Idk I think that’s more efficient I guess than a ddos. Spend some extra time and don’t get busted why not lol. I can’t really think of anything because, I do not have any big companies I’m after right now ha ha!
Now, being a script kiddie and using other line user interface tools? I wouldn’t really say that’s being a script kiddie. I mean depends on the extent you go to… Like if your using something that requires a lot of custom input and data that you’re retrieving on your own such as, net work maps, port scanning, database injection scanning, etc. and then inputting it in the software? Then “I” at least wouldn’t say that would be a script kiddie. Other, very “advanced” / egotistical people would beg to differ but y ‘know what… I’m not them! Now if you’re using a lot of button click / gui based stuff that’s like, “Enter Ip address… Okay hacking… loading…. hacked! Would you now like to see their screen? y o n? okay loading screen shot” then yeah I would or if it’s something simple like armitage then yeah…. script kiddie all the way. But, don’t condemn the script kiddies because, they’re learning y ‘know and we all start somewhere right?
Picking up Python is fairly easy since it’s plain English but it’s different in a weird way and idk how to explain check it out for yourself. Imagine if command line made a baby with a standard programming language. That’s what you would get I guess :/ there’s so much on codeacademy though seriously check it out. Backtrack was fun and had some cool linux stuff I’m not going into but the consistency with Kali and the stability is excellent unless you’re running from a usb then, the network drivers tend to give out. But that’s also when it was new, I’ll have to check back in, maybe see if KDE is in yet all they had was GNOME last.
Anyways thanks for responding to my post. I was hoping at least somebody would lol
Thanks for the reply mate.
Just on the topic of Script Kiddies, I know I’m new here, but that codeacademy website is great! I’m doing HTML and Javascript, and will be starting PHP when I finish HTML (around 60%). I use the metasploit command interface as I want to see the different options better, and its easier for me to understand (and I can’t afford all this ‘auto select exploit’ stuff on the Web GUI!). But i’m starting off with it, and if yo have any experience with metasploit could you please check my post in the Tools & Utilities forum, i’m sort of stuck with metasploit, and google isn’t going anywhere… Thanks! (Sorry to Mods for deviating…)
LOIC (low orbit ion cannon) – DOS attacking tool
The DOS (Denial of service) attack is one of the more powerful hacks, capable of completely taking a server down. In this way, the server will not be able to handle the requests of valid users. With a DOS attack, many computer systems connected to the internet will try to flood a server with false requests, leading to a service disruption. There are many ways in which an attacker can enact this attack on a server system over the network or the internet. Some hackers try this attack with their own coded tools while others use previously available tools.
A LOIC (Low Orbit Ion Cannon) is one of the most powerful DOS attacking tools freely available. If you follow news related to hacking and security issues, you doubtless have been hearing about this tool for the past several months. It has become widely used, including in some highly-publicized attacks against the PayPal, Mastercard and Visa servers a few months back. This tool was also the weapon of choice implemented by the (in)famous hacker group, Anonymous, who have claimed responsibility for many high profile hacking attacks, among them, hacks against Sony, the FBI and other US security agencies. The group not only used this tool, but also requested that others download it and join Anonymous attacks via IRC.
In this brief article, I will give an overview and operational model of the tool. There are 2 versions of the tool: the first is the binary version, which is the original LOIC tool. The other is web-based LOIC or JS LOIC.
Figure 1: Original LOIC
About the original LOIC tool
The LOIC was originally developed by Praetox Technologies as a stress testing application before becoming available within the public domain. The tool is able to perform a simple dos attack by sending a large sequence of UDP, TCP or HTTP requests to the target server. It’s a very easy tool to use, even by those lacking any basic knowledge of hacking. The only thing a user needs to know for using the tool is the URL of the target. A would-be hacker need only then select some easy options (address of target system and method of attack) and click a button to start the attack.
The tool takes the URL of the target server on which you want to perform the attack. You can also enter the IP address of the target system. The IP address of the target is used in place of an internal local network where DNS is not being used. The tool has three chief methods of attack: TCP, UDP and HTTP. You can select the method of attack on the target server. Some other options include timeout, TCP/UDP message, Port and threads. See the basic screen of the tool in the snapshot above in Figure 1.
The LOIC version used by Anonymous group attacks was different than the original LOIC. It had an option to connect the client to the IRC (Internet Relay Chat). This allowed the tool to be remotely controlled, using the IRC protocol. In that case, the user machine became part of a botnet. A botnet is a system of compromised computer systems connected to each other via the internet, which are in turn controlled by the attacker who directs the malware toward his / her target. The bigger the botnet, the more powerful the attack is.
Figure 2: Modified version of LOIC with an option for IRC connect
Type of attacks
As I’d mentioned previously, the LOIC uses three different types of attacks (TCP, UDP and HTTP). All three methods implement the same mechanism of attack. The tool opens multiple connections to the target server and sends a continuous sequence of messages which can be defined from the TCP/UDP message parameter option available on the tool. In the TCP and UDP attacks, the string is sent as a plain text but in the HTTP attack, it is included in the contents of a HTTP GET message.
This tool continues sending requests to the target server; after some time, the target server becomes overloaded. In this way, the target server will no longer be able to respond to requests from legitimate users, effectively shutting it down.
Analysis of the attack
UDP Attack: To perform the UDP attack, select the method of attack as UDP. It has port 80 as the default option selected, but you can change this according to your need. Change the message string or leave it as the default.
TCP Attack: This method is similar to UDP attack. Select the type of attack as TCP to use this.
HTTP Attack: In this attack, the tool sends HTTP requests to the target server. A web application firewall can detect this type of attack easily.
How to use LOIC to perform a Dos attack: Just follow these simple steps to enact a DOS attack against a website (but do so at your own risk).
Figure3: LOIC in action (I painted the URL and IP white to hide the identity of the victim in snap)
After starting the attack you will see some numbers in the Attack status fields. When the requested number stops increasing, restart the LOIC or change the IP. You can also give the UDP attack a try. Users can also set the speed of the attack by the slider. It is set to faster as default but you can slow down it with the slider. I don’t think anyone is going to slow down the attack.
Here’s the meaning of each field:
LOIC in HIVEMIND
The windows version of LOIC has a feature called HIVEMIND. With this, users can connect their client to an IRC server. In this way, it can be controlled remotely, thus facilitating some risky attacks, so use this wisely. But connecting to an IRC server will not allow a remote administration of your machine or any other risks to your system: it will only control your LOIC client. This method was used to collect more people in the DDOS attack against Visa, Mastercard, and other financial organizations that supported Wikileaks. (The attack was called “Operation Pay-back.”)
In this mode, thousands of system attacks on a single website to made a real impact. The more people that joined the attack via IRC, the more powerful the attack became.
To start LOIC in HIVEMIND mode, run this command in the command prompt:
LOIC.exe /hivemind irc.server.address
After running the above command, your LOIC client will connect to irc://irc.server.adress:6667/loic
You can also set more parameters in the command to use the tool in better way. Use port and channel too with the command.
LOIC.exe /hivemind irc.server.address 1234 #secret
It will connect to irc://irc.server.adress:1234/secret
Hidden mode
You can also run your LOIC in hidden mode while using it in HIVEMIND. Running in hidden mode means LOIC will run without any visible GUI at your windows system. Just add /HIDDDEN in your command.
LOIC.exe /hidden /hivemind irc.server.address
It will connect LOIC client to irc://irc.server.adress:6667/loic without any visible GUI on windows.
Web-based LOIC (JS LOIC)
This version of LOIC was released on 9 th December, 2010. This web- based tool runs only on JavaScript-enabled web browsers. In JS LOIC, JS stands for JavaScript This version of LOIC sends an ID and message with lots of connections with each ID and message. This is easier to use than the desktop version. Just visit the web page with a single HTML file and start the attack. The attack power of this version is same as from the desktop.
Drawbacks of using LOIC
The main drawback of LOIC as a DOS attack tool is that it is very easy to find the attacker. This tool does not take any precautions to hide IP address of the origin of the attack. Attacks generated by this tool are simple and expose the IP address of attacker in each request packet sent to victim server to flood the request queue. If you are thinking that we can use proxies to solve this problem, you are wrong. Attackers cannot use proxies in these attacks because your requests will hit the proxy server, not the target server. So you will not be able to launch a DOS attack on the server effectively while using a proxy. But some analysts say that this can be used with a proxy server if the proxy is robust enough. According to them, all your request packets will be forwarded to the server system by proxy at the end.
How to prevent the attack of LOIC
LOIC is available for free to download and use, and can be used effectively with very little hacking experience. Anyone that wants to can attack a website with this tool.
As discussed above, the attack of this tool is simple and easy to identify. A well-configured firewall is enough to prevent the attack from being fully effective. And a server administrator can see the request logs to identify the IP and block the IP from the server. Every website owner or server administrators should monitor the traffic and all the activities being performed on the server. This can help well enough against the attack. But this will not help you when a network of LOIC clients will fire on the server system all at once. Protecting the server with a Firewall configured to filter the packets sent by the LOIC is the best way to protect against the attack.
Conclusion
In past few months, this tool was downloaded millions of times and used against some big websites such as Mastercard, Visa, and PayPal to support Wikileaks. The group known as Anonymous used this tool to attack these websites, but it was not traceable. A lot of people joined the team with the IRC network, so no one knows who the real persons behind the group were, within such a large network of systems used in the attacks.
Use of this tool means sending some one threatening messages with your address and phone number. You will be easily caught. In some countries, a DOS attack is not illegal. You can use this tool as an individual, but this tool is not going to help you if you will use it with your system alone. You will need a network of systems to join your attack. This tool is easy to use and see the demonstration of DOS attack. But try it on your own risk.
This tool is available for free on the internet so any person can download it and create a problem for any website. Although catching the attacker is easy, protection against such an attack is relatively easy to achieve. I suggest each company and server administrator make sure that their firewall is configured to protect from the attack generated by LOIC.
What is Low Orbit Ion Cannon (LOIC)
For a tool that can cause serious damage to a website, LOIC is relatively simple. What it does basically is to send multiple requests and flood a targeted IP with TCP or UDP packets or HTTP requests.
One person cannot single handedly use LOIC to cause DoS, so a number of users have to come together to attack the website of a target, slow down its server by sending multiple requests and causing traffic.В
The Low Orbit Ion Cannon has enjoyed mass adoption because of its simplicity, anybody can use it. The best way to carry out a coordinated attack is in hivemind mode. This mode allows the group of attackers connects to an IRC (Internet Relay Chat) channel.В
The attackers send a command through the hivemind mode, this command contains attack details and target systems. This mode allows one user gain full control over the LOIC. This is achievable with the use of a voluntary botnet.В
LOIC has limitations, probably because it was not originally designed to serve this purpose (this will be discussed in this article). For starters, there is no anonymity, or redirecting through proxy, your identity can easily be traced and you can be prosecuted for carrying out a DoS attack. Identifying and blocking DoS attacks carried out through LOIC is easy because all requests come through one template. That’s probably why the hack group Anonymous crashed HOIC, a supposed improvement from LOIC.В
What is LOIC?
The Low Orbit Ion Cannon (LOIC) used to be a network stress testing application but now used for DoS and DDoS attacks.В
The Low Orbit Ion Cannon (LOIC) used to be a private stress testing software developed by Praetox Technology. Over time, it became open-source. straightforward
Since it became accessible to the public, people have hijacked them to launch DoS and DDoS attacks and are mostly used for malicious purposes.В
Despite its potential of causing harm, it is accessible and straightforward to use; this means you don’t need technical knowledge to launch a DoS and DDoS attack.В
The Low Orbit Ion Cannon is responsible for many attacks, including attacks from members of hacktivist group Anonymous, also among users of the 4Chan forums.; this.
There is a rise in the tool probably because it is easy to use, and easy to access. You can download the tool from the internet without restriction, its interface is easy to navigate, so you can launch an attack within minutes.В
LOIC originally was a Windows software written in C#. It initially became available on Sourceforge, an open-source program. Over time, it became available to other operating systems like Linux, OS X, Android, iOS.В
You can access the tool from a web browser using its JS LOIC version and a web version known as the Low Orbit Web Cannon.
Low Orbit Web Cannon has been in the news for a lot of negative reasons, some of the high profile attacks associated with DDoS includes:
Project Chanology – In 2008, the Church of Scientology issued a complaint about a copyright violation for some of its videos that were put up on YouTube. In response to the complaint, an attack was launched.В
Operation Payback –This was a malicious attack that took place in 2010, it was a viral campaign that targeted organizations that opposed Wikileaks, Visa, MasterCard, PayPal, Sony, and PlayStation networks were all targets.
Operation Megaupload: In 2012, after the shutdown of Megaupload, there was an attack against all parties involved in the shutdown. It targeted organizations like; Universal Music Group, the US Department of Justice, and more.В
To get a better grasp of LOIS, you must first understand what DOS and DDoS are all about.В
Denial Of Service
Denial-Of-Service or DOS is like the first step of every newbie hacker, it is a prevalent hack methodology used worldwide to hack networks and bring down their target services.В
What it does is block the server making it incapable of accepting requests from valid visitors.В
There are DOS and DDoS, they mean the same thing, the only difference is;
Once an attack is carried out on a vulnerable server using a single IP, the attacker sends multiple overwhelming requests to the target when the target tries to reply to each of the packet requests, there’s going to be a jam because the request flow will overwhelm bandwidth (because it has exceeded the accepting capacity). There will no longer be room for new connections, this inevitably leads to denial of service for new connections.В
You can prevent this with the help of modern firewalls. All you need to do is attach a patch script to them. With this, you can customize the number of connections an IP or IP range can provide.
On the other hand, Distributed DOS Attack or DDOS is carried out through Botnets.В
Botnets are generated by sending out bait links or attachments, once they fall for the trap, the hacker will access the internet, webcams, or smart devices.
Once the hacker gains Botnets, he probably has pre-instructed it to carry out a DOS attack by causing the devices gained through Botnets to carry out a DOS attack on its target.В
Once the attack is launched, the target gets overwhelmed by request’s from multiple IP’s over the internet this leads to breakdown of its server.В
The difference between DDoS and DOS is that DDoS uses multiple IPs. Since there are multiple IP’s, you’ll have a huge task of blocking the many IP’s. That’s not the worst, distinguishing legitimate users’ data packets is where the job is.В
How LOIC works
The entire process is simple, it’s just about jamming the target server with TCP, UDP, or HTTP packets, this will disrupt the service server. This requires a collective effort of people with the same intent.В
Using LOIC is surprisingly easy, it can be accessed either through a specific IP address using either TCP or UDP packets or the HTTP requests to a specific port.В
One person can not single-handedly launch an attack, so he will need to collaborate with a number of other users. The idea is to use LOIC to target a server and with their numbers, they will slow or interrupt the server with the unusual high network traffic.
Just like I stated already, The Low Orbit Ion Cannon needs little or no technical knowledge to operate, once you are familiar with basic technologies like mobile phones or even pc, using the Low Orbit Ion Cannon will be easy. If you want to launch an organized DDoS attack, you can use the application in hivemind mode.В
The hivemind mode allows you to only connect to the Internet Relay Chat channel. This mood also allows one person to gain total control of LOIC instances on many user computers so the attack is performed by a voluntary botnet.
Although easy to use, the LOIC has its downside, every person that initiated the attack can easily hide identity or redirected through proxies. Hence if you participate in a DDoS attack using LOIC, you can easily be tracked and persecuted.В
Defending a DDoS launched through LOIC can easily be blocked since requests follow one channel. However, there’s a more technical version known as the High Orbit Ion Cannon (HOIC).В
Type of attacks
DOS through LOIC allows you to open multiple connections to target the server by sending continuous strings of messages recognizable by the TCP/UDP message parameter option on the software.В
During a typical TCP and UDP attack, you’ll send the string as regular text, for an HTTP attack, it comes as HTTP GET message.
В UDP AttackВ
Here’s the code that represents the Snort rule:
TCP Attack:В
HTTP Attack:В
Here’s the code that represents the HTTP Attack:
Downloading:
LOIC can be gotten faster than ordering a pizza. All you need to do is search LOIC on Google and you are good to go. It is better if you are using Linus Distributions (Kali Linux).В
Once you have the software downloaded, run it. The first requirement is for you to provide the IP or URL of your target in a section called Target Section 1, you’ll see it in the selected target box.
After you are done, choose an attack method then monitor your attack status.В
Go into the slider then set the speed of the attack, by default its speed is meant to be fast, but you can slow down the pace. Here are some fields and their meaning.В
IDLE: This helps you monitor threads that are idle. If it stays at zero, the attack would be more effective.В
Connecting: This is how you know the number of connections that attempt to connect to the targeted server.В
Requesting: Here is where you can see the number of connections that are demanding information from the target’s server.В
Downloading: This displays all connections trying to initiate the download for information on the server.В
Downloaded: This displays number of times data initiated from the victim’s server is being downloaded.В
Requested: This stat shows how many times a data download has been requested from the victim server.
This shows the number of times a data request is made for data downloaded from the victim’s server.В
Failed: This gives you a state for the number of times the server fails to respond to requests. If you notice a huge number of fails, then it means the server is about to go down or is already down. The success of a DOS attack is measured by the higher n of failed.В
How to defend against LOIC attacks
Now that we understand how LOIC works, let’s have a look at how to prevent it.В
The best way to prevent a LOIC attack is through your internet service provider. If you are using a large internet provider, there’s a good chance that it already has a DDoS mitigation mechanism. Just check for a cloud storage provider that already has a high bandwidth than LOIC, with this, LOIC attacks will not be able to cause harm.В
However, if you are hosting your personal web server, you will have to defend against LOIC by yourself. Hence, you will need intrusion detection and prevention systems such as Snort. If you dictate a LOIC attack, all you need to do is to filter out all the packets from specific IPs.В
Another method is to configure your firewall to restrict the number of requests per minute. With the restriction, you will be able to filter out attack traffic without affecting your legitimate users.В
Here’s another way to look at it
If it is a small LOIC HTTP attack, it can be protected by your local firewall; your service providers will look at the log and identify your attacker’s IP, push out them out, and reject their requests. This is easy to do because your service provider does the job. However, if there is a large-scale attack, this method won’t help much.В
If there are TCP or UDP floods, your local firewalls are incapable of handling them. UDP is so dangerous that it can disrupt a firewall.В
So what’s the way out?В
A Web Application Firewall (WAF) is stronger and can help protect against HTTP floods
Overall it is easy to detect attackers that use the LOIC. Their IP can be seen and since countries like U.S., U.K., Spain, and Turkey have laws to prosecute hackers, there is a reduction in the number of people using the platform.В
If the attacking threat is on small scale, you can manually detect and blocked through just with the help of your network traffic monitors and firewalls. However, some attacks are more severe and better coordinated, in such cases, you can only prevent them with the help of a dedicated security solution.
One good dedicated security solution is Imperva Website Protection. It is equipped to analyze incoming HTTP/S traffic, it also helps stop other attempts from LOIC TCP and HTTP floods.
Imperva DDoS protection another software you should try is equipped to protect against UDP attacks. This software utilizes Anycast technology to identify and block suspicious attacks in deep packet inspection.
How-To: Use (LOIC) Low Orbit Ion Cannon On Linux
Share this:
Compiling and Using Low Orbit Ion Cannon on Linux
This will help you get Low Orbit Ion Cannon (LOIC) running on Linux. A lot of the how-to’s out there for this are outdated and aren’t entirely relevant any longer.
I know for a fact it works with Xubuntu 13.04, so it should work with other Ubuntu variants as well, probably even Debian.
First, you’ll need to install mono-gmcs, mono-mcs, monodevelop, and liblog4net-cil-dev. You can install them like so:
Running that will install all the packages you need to compile LOIC with Mono. Those 4 packages have other dependencies, so you’ll actually end up installing many more packages, but it’ll be done automatically.
Once you’re in the folder, type the following in your terminal:
That will compile LOIC, the executable will be in the debug folder that you extracted from the zip or tar.gz file you downloaded. After compiling is done, launch LOIC like so:
That’s it, have fun! And don’t get in trouble.
Well, now what?
Work with Me
I’m available for hire and always taking new clients, big and small. Got a project or an idea you’d like to discuss? Startup plan but no developer to make it happen? Just get in touch, I’d love to see if I can help you out!
Leave some Feedback
Got a question or some updated information releavant to this post? Please, leave a comment! The comments are a great way to get help, I read them all and reply to nearly every comment. Let’s talk. 😀
Longren.io is proudly hosted by DigitalOcean
Share this:
Like this:
Related
Published by Tyler Longren
Hi! I’m Tyler Longren, a freelance web developer. I’m a father to two beautiful daughters and a car stereo enthusiast. I like PHP, JavaScript, WordPress, Git, HTML5 & CSS3, and other neat things. I really love the open source community, too. You can find me on twitter or Google+, and Github. This is my personal blog and that’s it! View all posts by Tyler Longren
25 thoughts on “ How-To: Use (LOIC) Low Orbit Ion Cannon On Linux ”
Hello I have tried this running Linux mint 12 and I have encountered a couple of problems, the first is that there is no Dubug folder in the bin and while compiling there were two error messages that said it couldnt find mono or a C# compiler. I would appreciate any help you could give me because I am a total noob at Linux. Thanks for your time.
Miller, try this:
After I ran that, I was able to get “mdtool build” to run without any errors. I think there was one warning, but it was something that could be ignored.
Let me know if this helps any.
Thank you tyler for that and I was able to get no error messages during the mdtool build, but I still do not know where it puts the finished product. As I said I am a total noob so sorry if I am missing something obvious.
OK, finished executable should be in NewEraCracker-LOIC-c847036/bin/Debug/.
Open a terminal and go into the NewEraCracker-LOIC-c847036 folder and type the following:
If everything worked, running that should launch LOIC.
Okay thank you for all your help
Let me know if that worked for you or not. If it didn’t work, it’s possible there’s something else missing that I already had installed, that you may need to install as well. And if that’s the case I’ll need to update this how-to.
It worked and it will probably work for others, I am just very new to Linux.
Ok so i tried DOSing a website on my local network. I used LOIC on both linux and windows and the site wasnt even affected. The numbers on the bottom bar seemed correct. WTF?!
ive confirmed that traffic is leaving the attacking machine and also confirmed that the packets are hitting the webserver.
Yah you probably wouldn’t see much affect doing it over your local network. About the only way to confirm it’s working is to monitor traffic on your network with a tool like WireShark.
How did you end up verifying that packets were actually being sent?
Wireshark 🙂 Also checked the logs of the webserver and verified that the packets are being received.
i got this error mssge
btw OS linux Slackware
Rep: Reputation: Disabled
Unhappy loic on linux slackware
i’ve install loic and mono using sbopkg
but loic can run and i got this mssge