This certificate confirms that
This certificate confirms that
this certificate presented to
1 невыполнение данного (требования)
2 невыполнение данного (требования)
См. также в других словарях:
Certificate of Merit Medal — Medal ribbon bar Awarded by United … Wikipedia
Certificate authority — In cryptography, a certificate authority, or certification authority, (CA) is an entity that issues digital certificates. The digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others… … Wikipedia
Certificate policy — A certificate policy is a document which aims to state what are the different actors of a public key infrastructure (PKI), their roles and their duties. This document is published in the PKI perimeter. When in use with X.509 certificates, a… … Wikipedia
Leaving Certificate — The Leaving Certificate ( ga. Ardteistiméireacht), commonly referred to as the Leaving Cert (Irish: Ardteist ) is the final course in the Irish secondary school system and culminates with the Leaving Certificate Examination. It takes a minimum of … Wikipedia
Extended Validation Certificate — Extended Validation Certificates (EV) [ The term validation as used here should not be confused with the Certification path validation algorithm commonly found in a certificate context.] are a special type of X.509 certificate which require more… … Wikipedia
China Compulsory Certificate — The China Compulsory Certificate mark, commonly known as CCC Mark, is a compulsory safety mark for many products sold on the Chinese market. It became effective on May 1, 2002. It is the result of the integration of China s two old compulsory… … Wikipedia
EUR.1 movement certificate — NOTOC EUR.1 is the name for a form, which is used in international commodity traffic. The application of this form is based on application of various bi and multilateral agreements within the Pan European preference system (the European Union… … Wikipedia
Erasmus of Arcadia — This article discusses Erasmus, the Greek Orthodox bishop. For other meanings, see Erasmus (disambiguation). Erasmus Εράσμους Bishop of Arcadia Church Greek Orthodox Church See Diocese of Arcadia In Office … Wikipedia
Republic of China passport — This article deals with passports issued by the Republic of China (Taiwan). For passports issued by the People s Republic of China, see People s Republic of China passport. Cover of the Republic of China biometric passport issued in 2009. The… … Wikipedia
Awards and decorations of the Civil Air Patrol — A Civil Air Patrol Cadet Captain in his Service Dress Uniform. Ribbons worn over the left pocket represent awards and achievements. Other various Badges and insignia are worn as well, in this case, the Cadet Solo Wings over the ribbons, and the… … Wikipedia
Academy Honorary Award — The Academy Honorary Award, instituted in 1948 for the 21st Academy Awards (previously called the Special Award), is given by the discretion of the Board of Governors of the Academy of Motion Picture Arts and Sciences (AMPAS) to celebrate motion… … Wikipedia
How does SSL really work?
How does SSL work?
Where is the certificate installed on the client (or browser?) and the server (or web server?)?
How does the trust/encryption/authentication process start when you enter the URL into the browser and get the page from the server?
How does the HTTPS protocol recognize the certificate? Why can’t HTTP work with certificates when it is the certificates which do all the trust/encryption/authentication work?
4 Answers 4
Trending sort
Trending sort is based off of the default sorting method — by highest score — but it boosts votes that have happened recently, helping to surface more up-to-date answers.
It falls back to sorting by highest score if no posts are trending.
Switch to Trending sort
Note: I wrote my original answer very hastily, but since then, this has turned into a fairly popular question/answer, so I have expanded it a bit and made it more precise.
TLS Capabilities
«SSL» is the name that is most often used to refer to this protocol, but SSL specifically refers to the proprietary protocol designed by Netscape in the mid 90’s. «TLS» is an IETF standard that is based on SSL, so I will use TLS in my answer. These days, the odds are that nearly all of your secure connections on the web are really using TLS, not SSL.
TLS has several capabilities:
#1 and #2 are very common. #3 is less common. You seem to be focusing on #2, so I’ll explain that part.
Authentication
A server authenticates itself to a client using a certificate. A certificate is a blob of data[1] that contains information about a website:
You can achieve confidentiality (#1 above) by using the public key included in the certificate to encrypt messages that can only be decrypted by the corresponding private key, which should be stored safely on that server.[2] Let’s call this key pair KP1, so that we won’t get confused later on. You can also verify that the domain name on the certificate matches the site you’re visiting (#2 above).
But what if an adversary could modify packets sent to and from the server, and what if that adversary modified the certificate you were presented with and inserted their own public key or changed any other important details? If that happened, the adversary could intercept and modify any messages that you thought were securely encrypted.
To prevent this very attack, the certificate is cryptographically signed by somebody else’s private key in such a way that the signature can be verified by anybody who has the corresponding public key. Let’s call this key pair KP2, to make it clear that these are not the same keys that the server is using.
Certificate Authorities
So who created KP2? Who signed the certificate?
Oversimplifying a bit, a certificate authority creates KP2, and they sell the service of using their private key to sign certificates for other organizations. For example, I create a certificate and I pay a company like Verisign to sign it with their private key.[3] Since nobody but Verisign has access to this private key, none of us can forge this signature.
And how would I personally get ahold of the public key in KP2 in order to verify that signature?
Well we’ve already seen that a certificate can hold a public key — and computer scientists love recursion — so why not put the KP2 public key into a certificate and distribute it that way? This sounds a little crazy at first, but in fact that’s exactly how it works. Continuing with the Verisign example, Verisign produces a certificate that includes information about who they are, what types of things they are allowed to sign (other certificates), and their public key.
Now if I have a copy of that Verisign certificate, I can use that to validate the signature on the server certificate for the website I want to visit. Easy, right?!
Well, not so fast. I had to get the Verisign certificate from somewhere. What if somebody spoofs the Verisign certificate and puts their own public key in there? Then they can forge the signature on the server’s certificate, and we’re right back where we started: a man-in-the-middle attack.
Certificate Chains
Continuing to think recursively, we could of course introduce a third certificate and a third key pair (KP3) and use that to sign the Verisign certifcate. We call this a certificate chain: each certificate in the chain is used to verify the next certificate. Hopefully you can already see that this recursive approach is just turtles/certificates all the way down. Where does it stop?
Since we can’t create an infinite number of certificates, the certificate chain obviously has to stop somewhere, and that’s done by including a certificate in the chain that is self-signed.
I’ll pause for a moment while you pick up the pieces of brain matter from your head exploding. Self-signed?!
Yes, at the end of the certificate chain (a.k.a. the «root»), there will be a certificate that uses it’s own keypair to sign itself. This eliminates the infinite recursion problem, but it doesn’t fix the authentication problem. Anybody can create a self-signed certificate that says anything on it, just like I can create a fake Princeton diploma that says I triple majored in politics, theoretical physics, and applied butt-kicking and then sign my own name at the bottom.
The [somewhat unexciting] solution to this problem is just to pick some set of self-signed certificates that you explicitly trust. For example, I might say, «I trust this Verisign self-signed certificate.»
With that explicit trust in place, now I can validate the entire certificate chain. No matter how many certificates there are in the chain, I can validate each signature all the way down to the root. When I get to the root, I can check whether that root certificate is one that I explicitly trust. If so, then I can trust the entire chain.
Conferred Trust
Authentication in TLS uses a system of conferred trust. If I want to hire an auto mechanic, I may not trust any random mechanic that I find. But maybe my friend vouches for a particular mechanic. Since I trust my friend, then I can trust that mechanic.
When you buy a computer or download a browser, it comes with a few hundred root certificates that it explicitly trusts.[4] The companies that own and operate those certificates can confer that trust to other organizations by signing their certificates.
This is far from a perfect system. Some times a CA may issue a certificate erroneously. In those cases, the certificate may need to be revoked. Revocation is tricky since the issued certificate will always be cryptographically correct; an out-of-band protocol is necessary to find out which previously valid certificates have been revoked. In practice, some of these protocols aren’t very secure, and many browsers don’t check them anyway.
Sometimes an entire CA is compromised. For example, if you were to break into Verisign and steal their root signing key, then you could spoof any certificate in the world. Notice that this doesn’t just affect Verisign customers: even if my certificate is signed by Thawte (a competitor to Verisign), that doesn’t matter. My certificate can still be forged using the compromised signing key from Verisign.
This isn’t just theoretical. It has happened in the wild. DigiNotar was famously hacked and subsequently went bankrupt. Comodo was also hacked, but inexplicably they remain in business to this day.
Even when CAs aren’t directly compromised, there are other threats in this system. For example, a government use legal coercion to compel a CA to sign a forged certificate. Your employer may install their own CA certificate on your employee computer. In these various cases, traffic that you expect to be «secure» is actually completely visible/modifiable to the organization that controls that certificate.
Some replacements have been suggested, including Convergence, TACK, and DANE.
Endnotes
[1] TLS certificate data is formatted according to the X.509 standard. X.509 is based on ASN.1 («Abstract Syntax Notation #1»), which means that it is not a binary data format. Therefore, X.509 must be encoded to a binary format. DER and PEM are the two most common encodings that I know of.
[2] In practice, the protocol actually switches over to a symmetric cipher, but that’s a detail that’s not relevant to your question.
Configure infrastructure to support SCEP with Intune
Intune supports use of the Simple Certificate Enrollment Protocol (SCEP) to authenticate connections to your apps and corporate resources. SCEP uses the Certification Authority (CA) certificate to secure the message exchange for the Certificate Signing Request (CSR). When your infrastructure supports SCEP, you can use Intune SCEP certificate profiles (a type of device profile in Intune) to deploy the certificates to your devices.
The Certificate Connector for Microsoft Intune is required to use SCEP certificate profiles with Intune when you also use an Active Directory Certificate Services Certification Authority, also called a Microsoft CA. The connector isn’t supported on the same server as your issuing Certification Authority (CA). The connector isn’t required when using Third-party Certification Authorities.
The information in this article can help you configure your infrastructure to support SCEP when using Active Directory Certificate Services. After your infrastructure is configured, you can create and deploy SCEP certificate profiles with Intune.
Prerequisites for using SCEP for certificates
Before you continue, ensure you’ve created and deployed a trusted certificate profile to devices that will use SCEP certificate profiles. SCEP certificate profiles directly reference the trusted certificate profile that you use to provision devices with a Trusted Root CA certificate.
Servers and server roles
To support SCEP, the following on-premises infrastructure must run on servers that are domain-joined to your Active Directory, with the exception of the Web Application Proxy Server.
Certificate Connector for Microsoft Intune – The Certificate Connector for Microsoft Intune is required to use SCEP certificate profiles with Intune when you use a Microsoft CA. It installs on the server that also runs the NDES server role. However, the connector isn’t supported on the same server as your issuing Certification Authority (CA).
For information about the certificate connector, see:
Certification Authority – Use a Microsoft Active Directory Certificate Services Enterprise Certification Authority (CA) that runs on an Enterprise edition of Windows Server 2008 R2 with service pack 1, or later. The version of Windows Server you use must remain in support by Microsoft. A Standalone CA isn’t supported. For more information, see Install the Certification Authority.
If your CA runs Windows Server 2008 R2 SP1, you must install the hotfix from KB2483564.
NDES server role – To support using the Certificate Connector for Microsoft Intune with SCEP, you must configure the Windows Server that will host the certificate connector with the Network Device Enrollment Service (NDES) server role. The connector supports installation on Windows Server 2012 R2 or later. In a later section of this article, we guide you through installing NDES.
To learn more about NDES, see Network Device Enrollment Service Guidance in the Windows Server documentation, and Using a Policy Module with the Network Device Enrollment Service. To learn how to configure high availability for NDES, see High Availability.
Support for NDES on the internet
To allow devices on the internet to get certificates, you must publish your NDES URL external to your corporate network. To do this, you can use a reverse proxy like Azure AD Application Proxy, Microsoft’s Web Application Proxy Server, or a third-party reverse proxy service or device.
Azure AD Application Proxy – You can use the Azure AD Application Proxy instead of a dedicated Web Application Proxy (WAP) Server to publish your NDES URL to the internet. This solution allows both intranet and internet facing devices to get certificates. For more information, see Integrate with Azure AD Application Proxy on a Network Device Enrollment Service (NDES) server.
The server that hosts WAP must install an update that enables support for the long URLs that are used by the Network Device Enrollment Service. This update is included with the December 2014 update rollup, or individually from KB3011135.
The WAP server must have an SSL certificate that matches the name that’s published to external clients and trust the SSL certificate that’s used on the computer that hosts the NDES service. These certificates enable the WAP server to terminate the SSL connection from clients and create a new SSL connection to the NDES service.
Third-party reverse proxy – When you use a third-party reverse proxy, ensure that the proxy supports a long URI get request. As part of the certificate request flow, the client makes a request with the certificate request in the query string. As a result, the URI length can be large, up to 40 kb in size.
SCEP protocol limitations prevent use of pre-authentication. When you publish the NDES URL via a reverse proxy server you must have Pre Authentication set to Passthrough. Intune secures the NDES URL when you install the Intune Certificate connector, by installing an Intune-SCEP policy module on the NDES server. The module helps to secure the NDES URL by preventing certificates from being issued to invalid or digitally tampered certificate requests. This limits access to only Intune enrolled devices that you manage with Intune and that have well-formed certificate requests.
When an Intune SCEP certificate profile is delivered to a device, Intune generates a custom challenge blob that it encrypts and signs. The blob isn’t readable by the device. Only the policy module and the Intune service can read and verify the challenge blob. The blob includes details Intune expects will be provided by the device in its certificate signing request (CSR). For example, the expected Subject and Subject Alternative Name (SAN).
The Intune policy module works to secure NDES in the following ways:
When attempting to access the published NDES URL directly, the server returns a 403 – Forbidden: Access is denied response.
When a well-formed SCEP certificate request is received and the request payload includes both the challenge blob and the device CSR, the policy module compares the details of the device CSR against the challenge blob:
If the validation fails, no certificate is issued.
Only the certificate requests from an Intune enrolled device that passes the challenge blob validation are issued a certificate.
Accounts
To configure the connector to support SCEP, you’ll need an account that has permissions to configure NDES on the Windows Server and to manage your Certification Authority. For details, see Accounts in the Prerequisites for the Certificate Connector for Microsoft Intune article.
Network requirements
In addition to the network requirements for the certificate connector, we recommend publishing the NDES service through a reverse proxy, such as the Azure AD application proxy, Web Access Proxy, or a third-party proxy. If you don’t use a reverse proxy, then allow TCP traffic on port 443 from all hosts and IP addresses on the internet to the NDES service.
Allow all ports and protocols necessary for communication between the NDES service and any supporting infrastructure in your environment. For example, the computer that hosts the NDES service needs to communicate with the CA, DNS servers, domain controllers, and possibly other services or servers within your environment, like Configuration Manager.
Certificates and templates
The following certificates and templates are used when you use SCEP.
| Object | Details |
|---|---|
| SCEP Certificate Template | Template you’ll configure on your issuing CA used to fullfil the devices SCEP requests. |
| Server authentication certificate | Web Server certificate requested from your issuing CA or public CA. You install and bind this SSL certificate in IIS on the computer that hosts NDES. |
| Trusted Root CA certificate | To use a SCEP certificate profile, devices must trust your Trusted Root Certification Authority (CA). Use a trusted certificate profile in Intune to provision the Trusted Root CA certificate to users and devices. — Use a single Trusted Root CA certificate per operating system platform and associate that certificate with each trusted certificate profile you create. — You can use additional Trusted Root CA certificates when needed. For example, you might use additional certificates to provide a trust to a CA that signs the server authentication certificates for your Wi-Fi access points. Create additional Trusted Root CA certificates for issuing CAs. In the SCEP certificate profile you create in Intune, be sure to specify the Trusted Root CA profile for the issuing CA. For information about the trusted certificate profile, see Export the trusted root CA certificate and Create trusted certificate profiles in Use certificates for authentication in Intune. |
The following certificate is not used with the Certificate Connector for Microsoft Intune. This information is provided for those who have not yet replaced the older connector for SCEP (installed by NDESConnectorSetup.exe) with the new connector software.
| Object | Details |
|---|---|
| Client authentication certificate | Requested from your issuing CA or public CA. You install this certificate on the computer that hosts the NDES service and it’s used by the Certificate Connector for Microsoft Intune. If the certificate has the client and server authentication key usages set (Enhanced Key Usages) on the CA template that you use to issue this certificate, you can then use the same certificate for server and client authentication. |
PIN requirement for Android Enterprise
For Android Enterprise, the version of encryption on a device determines whether the device must be configured with a PIN before SCEP can provision that device with a certificate. The available encryption types are:
Full-disk encryption, which requires the device have a PIN configured.
File-based encryption, which is required on devices that are installed by the OEM with Android 10 or later. These devices won’t require a PIN. Devices that upgrade to Android 10 might still require a PIN.
Microsoft Endpoint Manager can’t identify the type of encryption on an Android device.
The version of Android on a device can affect the available encryption type:
Android 10 and later: Devices installed with Android 10 or later by the OEM will use file-based encryption and won’t require a PIN for SCEP to provision a certificate. Devices that upgrade to version 10 or later and begin to use file-based encryption might still require a PIN.
Android 8 to 9: These versions of Android support the use of file-based encryption, but it’s not required. Each OEM chooses which encryption type to implement for a device. It’s also possible that OEM modifications will result in a PIN not being required even when full-disk encryption is in use.
For more information, see the following articles in the Android documentation:
Considerations for devices enrolled as Android Enterprise dedicated
For devices enrolled as Android Enterprise dedicated, password enforcement can present challenges.
For devices that run 9.0 and later and receive a kiosk-mode policy, you can use a device compliance or device configuration policy to enforce the password requirement. View Support Tip: New Google-based Compliance Screens for Kiosk Mode from the Intune Support Team, to understand the device experience.
For devices that run 8.x and earlier, you can also use a device compliance or device configuration policy to enforce the password requirement. However, to set up a PIN, you’ll need to manually enter the settings application on the device and configure the PIN.
Configure the certification authority
In the following sections, you’ll:
The following sections require knowledge of Windows Server 2012 R2 or later, and of Active Directory Certificate Services (AD CS).
Access your Issuing CA
Sign in to your issuing CA with a domain account with rights sufficient to manage the CA.
Open the Certification Authority Microsoft Management Console (MMC). Either Run ‘certsrv.msc’ or in Server Manager, click Tools, and then click Certification Authority.
Select the Certificate Templates node, click Action > Manage.
Create the SCEP certificate template
Create a v2 Certificate Template (with Windows 2003 compatibility) for use as the SCEP certificate template. You can:
Configure the following settings on the specified tabs of the template:
General:
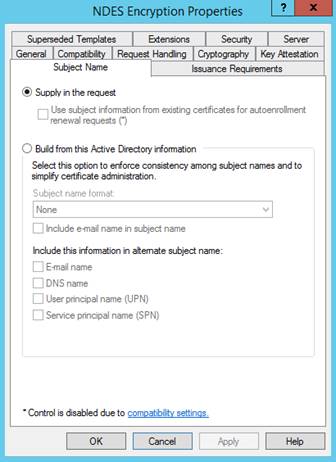
Subject Name:
Select Supply in the request. Security is enforced by the Intune policy module for NDES.
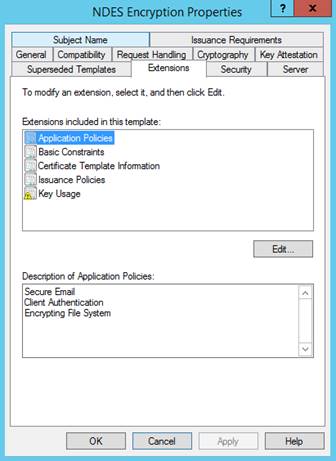
Extensions:
Ensure that Description of Application Policies includes Client Authentication.
Only add the application policies that you require. Confirm your choices with your security admins.
For iOS/iPadOS and macOS certificate templates, also edit Key Usage and make sure Signature is proof of origin isn’t selected.
Security:
Add the NDES service account. This account requires Read and Enroll permissions to this template.
Add additional Accounts for Intune administrators who will create SCEP profiles. These accounts require Read permissions to the template to enable these admins to browse to this template while creating SCEP profiles.
Request Handling:
The following image is an example. Your configuration might vary.
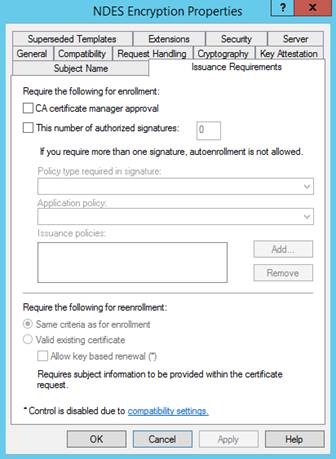
Issuance Requirements:
The following image is an example. Your configuration might vary.
Save the certificate template.
Create the client certificate template
The following certificate is not used with the Certificate Connector for Microsoft Intune. This information is provided for those who have not yet replaced the older connector for SCEP (installed by NDESConnectorSetup.exe) with the new connector software.
The Microsoft Intune Connector requires a certificate with the Client Authentication Enhanced Key Usage and Subject name equal to the FQDN of the machine where the connector is installed. A template with the following properties is required:
If you already have a template that includes these properties, you can reuse it, otherwise create a new template by either duplicating an existing one or creating a custom template.
Create the server certificate template
Communications between managed devices and IIS on the NDES server use HTTPS, which requires use of a certificate. You can use the Web Server certificate template to issue this certificate. Or, if you prefer to have a dedicated template, the following properties are required:
If you have a certificate that satisfies both requirements from the client and server certificate templates, you can use a single certificate for both IIS and the certificate connector.
Grant permissions for certificate revocation
For Intune to be able to revoke certificates that are no longer required, you must grant permissions in the Certificate Authority.
On the server that hosts the certificate connector, use either the NDES server system account or a specific account such as the NDES service account.
On your Certificate Authority console, Right-click the CA name and select Properties.
In Security tab, click Add.
Grant Issue and Manage Certificates permission:
Modify the validity period of the certificate template
It’s optional to modify the validity period of the certificate template.
After you create the SCEP certificate template, you can edit the template to review the Validity period on the General tab.
By default, Intune uses the value configured in the template, but you can configure the CA to allow the requester to enter a different value, so that value can be set from within the Intune console.
Plan to use a validity period of five days or greater. When the validity period is less than five days, there is a high likelihood of the certificate entering a near-expiry or expired state, which can cause the MDM agent on devices to reject the certificate before it’s installed.
For iOS/iPadOS and macOS, always use a value set in the template.
To configure a value that can be set from within the Intune console
On the CA, run the following commands:
Publish certificate templates
On the issuing CA, use the Certification Authority snap-in to publish the certificate template. Select the Certificate Templates node, select Action > New > Certificate Template to Issue, and then select the certificate template you created in the previous section.
Validate that the template has published by viewing it in the Certificate Templates folder.
Set up NDES
Install the NDES service
On the server that will host your NDES service, sign in as an Enterprise Administrator, and then use the Add Roles and Features Wizard to install NDES:
In the Wizard, select Active Directory Certificate Services to gain access to the AD CS Role Services. Select Network Device Enrollment Service, uncheck Certification Authority, and then complete the wizard.
In Installation progress, don’t select Close. Instead, select the Configure Active Directory Certificate Services on the destination server link. The AD CS Configuration wizard opens, which you use for the next procedure in this article, Configure the NDES service. After AD CS Configuration opens, you can close the Add Roles and Features wizard.
When NDES is added to the server, the wizard also installs IIS. Confirm that IIS has the following configurations:
Web Server > Security > Request Filtering
Web Server > Application Development > ASP.NET 3.5
Web Server > Application Development > ASP.NET 4.7.2
Management Tools > IIS 6 Management Compatibility > IIS 6 Metabase Compatibility
Management Tools > IIS 6 Management Compatibility > IIS 6 WMI Compatibility
On the server, add the NDES service account as a member of the local IIS_IUSR group.
On the computer that hosts the NDES service, run the following command in an elevated command prompt. The following command sets the SPN of the NDES Service account:
For example, if the computer that hosts the NDES service is named Server01, your domain is Contoso.com, and the service account is NDESService, use:
setspn –s http/Server01.contoso.com contoso\NDESService
Configure the NDES service
To configure the NDES service, use an account that is an Enterprise Administrator.
On the computer that hosts the NDES service, open the AD CS Configuration wizard, and then make the following updates:
If you’re continuing on from the last procedure and clicked the Configure Active Directory Certificate Services on the destination server link, this wizard should already be open. Otherwise, open Server Manager to access the post-deployment configuration for Active Directory Certificate Services.
After the wizard completes, update the following registry key on the computer that hosts the NDES service:
To update this key, identify the certificate templates’ Purpose (found on its Request Handling tab). Then, update the corresponding registry entry by replacing the existing data with the name of the certificate template (not the display name of the template) that you specified when you created the certificate template.
The following table maps the certificate template purpose to the values in the registry:
| Certificate template Purpose (On the Request Handling tab) | Registry value to edit | Value seen in the Intune admin console for the SCEP profile |
|---|---|---|
| Signature | SignatureTemplate | Digital Signature |
| Encryption | EncryptionTemplate | Key Encipherment |
| Signature and encryption | GeneralPurposeTemplate | Key Encipherment Digital Signature |
For example, if the Purpose of your certificate template is Encryption, then edit the EncryptionTemplate value to be the name of your certificate template.
Restart the server that hosts the NDES service. Don’t use iisreset; iireset doesn’t complete the required changes.
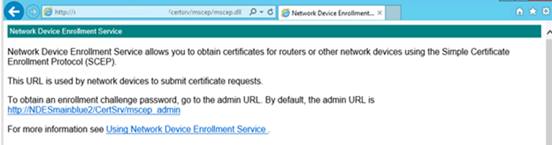
Browse to http://Server_FQDN/certsrv/mscep/mscep.dll. You should see an NDES page similar to the following image:
If the web address returns a 503 Service unavailable, check the computers event viewer. This error commonly occurs when the application pool is stopped due to a missing permission for the NDES service account.
Install and bind certificates on the server that hosts NDES
On the NDES server, add a Server authentication certificate.
Server authentication certificate
This certificate is used in IIS. It’s a simple Web server certificate that allows the client to trust NDES URL.
Request a server authentication certificate from your internal CA or public CA, and then install the certificate on the server.
Depending how you expose your NDES to the internet, there are different requirements.
A good configuration is:
If you are using Azure AD App Proxy, the AAD App Proxy connector will translate the requests from the external URL to the internal URL. As such, NDES will only respond to requests directed to the internal URL, usually the FQDN of the NDES Server.
In this situation, the external URL is not required.
Bind the server authentication certificate in IIS:
After installing the server authentication certificate, open IIS Manager, and select the Default Web Site. In the Actions pane, select Bindings.
Select Add, set Type to https, and then confirm the port is 443.
For SSL certificate, specify the server authentication certificate.
The following information is provided for those who have not yet replaced the older connector for SCEP (installed by NDESConnectorSetup.exe) with the new connector software.
Client authentication certificate
This certificate is used during install of the Certificate Connector for Microsoft Intune to support SCEP.
Request and install a client authentication certificate from your internal CA, or a public certificate authority.
The certificate must meet the following requirements:
Certification Authority Guidance
Applies To: Windows Server 2012 R2, Windows Server 2012
A certification authority (CA) is responsible for attesting to the identity of users, computers, and organizations. The CA authenticates an entity and vouches for that identity by issuing a digitally signed certificate. The CA can also manage, revoke, and renew certificates.
A certification authority can refer to following:
An organization that vouches for the identity of an end user
A server that is used by the organization to issue and manage certificates
By installing the Certification Authority role service of Active Directory Certificate Services (AD CS), you can configure your Windows server to act as a CA.
Before you install the CA role service, you should:
Plan a public key infrastructure (PKI) that is appropriate for your organization.
Install and configure a Hardware Security Module (HSM) according to the HSM vendor instructions, if you are planning to use one.
Create an appropriate CAPolicy.inf, if you want to modify the default installation settings.
Plan for PKI
To ensure that your organization can take full advantage of your Active Directory Certificate Services (AD CS) installation, you must plan the PKI deployment appropriately. You should determine how many CAs you will install and in what configuration before you install any CA. Creating an appropriate PKI design can be time consuming, but it is important for the success of your PKI.
For more information and resources, see PKI Design Guidance in Microsoft TechNet.
Use an HSM
Using a hardware security module (HSM) can enhance the security of the CA and the PKI.
An HSM is a dedicated hardware device that is managed separately from the operating system. These modules provide a secure hardware store for CA keys, in addition to a dedicated cryptographic processor to accelerate signing and encrypting operations. The operating system utilizes the HSM through the CryptoAPI interfaces, and the HSM functions as a cryptographic service provider (CSP) device.
HSMs typically are PCI adapters, but they are also available as network-based appliances, serial devices, and USB devices. If an organization plans to implement two or more CAs, you can install a single network-based HSM and share it among multiple CAs.
To set up a CA by using an HSM, the HSM must be installed and configured before you set up any CAs with keys that will be stored on the HSM.
Consider a CAPolicy.inf file
The CAPolicy.inf file is not required to install AD CS, but it can be used to customize the settings of the CA. The CAPolicy.inf file contains various settings that are used when installing a CA or when renewing the CA certificate. The CAPolicy.inf file must be created and stored in the %systemroot% directory (typically C:\Windows) for it to be used.
The settings that you include in the CAPolicy.inf file depend largely on the deployment type that you want to create. For example, a root CA might have a CAPolicy.inf file that looks like this:
Whereas a CAPolicy.inf file for an enterprise that is issuing a CA might look like this:
Select CA configuration settings
The following sections describe the configuration options that you will select after installing the CA binary installation files.
Select setup type
Enterprise CAs are integrated with Active Directory Domain Services (AD DS). They publish certificates and certificate revocation lists (CRLs) to AD DS. Enterprise CAs use information that is stored in AD DS, including user accounts and security groups, to approve or deny certificate requests. Enterprise CAs use certificate templates. When a certificate is issued, the Enterprise CA uses information in the certificate template to generate a certificate with the appropriate attributes for that certificate type.
If you want to enable automated certificate approval and automatic user certificate enrollment, use Enterprise CAs to issue certificates. These features are available only when the CA infrastructure is integrated with Active Directory. Additionally, only Enterprise CAs can issue certificates that enable smart card sign-in, because this process requires that smart card certificates are mapped automatically to the user accounts in Active Directory.
By default, you must be a member of the Enterprise Admins group to install and configure an Enterprise CA. If you want a low-privileged domain administrator to install and configure an Enterprise CA, see Delegated Installation for an Enterprise Certification Authority.
Stand-alone CAs do not require AD DS, and they do not use certificate templates. If you use stand-alone CAs, all information about the requested certificate type must be included in the certificate request. By default, all certificate requests that are submitted to stand-alone CAs are held in a pending queue until a CA administrator approves them. You can configure stand-alone CAs to issue certificates automatically upon request, but this is less secure, and it is usually not recommended because the requests are not authenticated.
From a performance perspective, using stand-alone CAs with automatic issuance enables you to issue certificates at a faster rate than you can by using enterprise CAs. However, unless you are using automatic issuance, using stand-alone CAs to issue large volumes of certificates usually comes at a high administrative cost because an administrator must manually review and then approve or deny each certificate request. For this reason, stand-alone CAs are best used with public key security applications on extranets and on the Internet, when users do not have user accounts and when the volume of certificates to be issued and managed is relatively low
You must use stand-alone CAs to issue certificates when you are using a non-Microsoft directory service or when AD DS is not available. You can use both enterprise and stand-alone certification authorities in your organization, as explained in the following table.
| Option | Enterprise CA | Standalone CA |
|---|---|---|
| Publish certificates in Active Directory and use Active Directory to validate certificate requests. | Yes | No |
| Take the CA offline. | Not recommended | Yes |
| Configure the CA to issue certificates automatically. | Yes | Not recommended |
| Allow administrators to approve certificate requests manually. | Yes | Yes |
| Allow for the use of certificate templates. | Yes | No |
| Authenticate requests to Active Directory. | Yes | No |
Choose CA type
Enterprise and stand-alone CAs can be configured as root CAs or as subordinate CAs. Subordinate CAs can further be configured as intermediate CAs (also referred to as a policy CA) or issuing CAs
Designate a root CA
A root CA is the CA that is at the top of a certification hierarchy. It must be trusted unconditionally by clients in your organization. All certificate chains terminate at a root CA. Whether you use enterprise or stand-alone CAs, you need to designate a root CA.
Since the root CA is the top CA in the certification hierarchy, the Subject field of the certificate that is issued by a root CA has the same value as the Issuer field of the certificate. Likewise, because the certificate chain terminates when it reaches a self-signed CA, all self-signed CAs are root CAs. The decision to designate a CA as a trusted root CA can be made at the enterprise level or locally by the individual IT administrator.
A root CA serves as the foundation upon which you base your certification authority trust model. It guarantees that the subject’s public key corresponds to the identity information shown in the subject field of the certificates it issues. Different CAs might also verify this relationship by using different standards; therefore, it is important to understand the policies and procedures of the root certification authority before choosing to trust that authority to verify public keys.
The root CA is the most important CA in your hierarchy. If your root CA is compromised, all CAs in the hierarchy and all certificates issued from it are considered compromised. You can maximize the security of the root CA by keeping it disconnected from the network and by using subordinate CAs to issue certificates to other subordinate CAs or to end users.
Subordinate CAs
CAs that are not root CAs are considered subordinate. The first subordinate CA in a hierarchy obtains its CA certificate from the root CA. This first subordinate CA can use this key to issue certificates that verify the integrity of another subordinate CA. These higher subordinate CAs are referred to as intermediate CAs. An intermediate CA is subordinate to a root CA, but it serves as a higher certifying authority to one or more subordinate CAs.
An intermediate CA is often referred to as a policy CA because it is typically used to separate classes of certificates that can be distinguished by policies. For example, policy separation includes the level of assurance that a CA provides or the geographical location of the CA to distinguish different end-entity populations. A policy CA can be online or offline.
It is not possible to convert a root CA to a subordinate CA, or vice versa.
Store a private key
The private key is part of the CA identity, and it must be protected from compromise. Many organizations protect CA private keys by using a hardware security module (HSM). If an HSM is not used, the private key is stored on the CA computer. For more information, see Hardware Security Module (HSM) in Microsoft TechNet.
Offline CAs should be stored in secure locations and not connected to the network. Issuing CAs use their private keys when issuing certificates, so the private key must be accessible (online) while the CA is in operation. In all cases, the CA and its private key on the CA should be physically protected.
Locate an existing key
If you already have an existing private key that you want to use during installation, you can use the Existing Key screen to locate that key. You can use the Change button to modify the cryptographic provider, and optionally, the CA that you want to search for an existing key.
Locate an existing certificate
If you already have a certificate that contains the private key for the CA, you can use the Existing Certificate screen to locate it. You can use the Import button to open the Import Existing Certificate dialog box, and then locate your existing PKCS #12 file.
Select cryptographic options
Selecting cryptographic options for a certification authority (CA) can have significant security, performance, and compatibility implications for that CA. Although the default cryptographic options may be suitable for most CAs, the ability to implement custom options can be useful to administrators and application developers with a more advanced understanding of cryptography and a need for this flexibility. Cryptographic options can be implemented by using cryptographic service providers (CSPs) or key storage providers (KSPs).
When using an RSA certificate for a CA, ensure that the key length is at least 2048 bits. You must not attempt to use an RSA certificate below 1024 bits for the CA. The CA service (certsvc) will not start if an RSA key of less than 1024 bits is installed.
CSPs are hardware and software components in Windows operating systems that provide generic cryptographic functions. CSPs can be written to provide a variety of encryption and signature algorithms.
KSPs can provide strong key protection for computers running a minimum server version Windows Server 2008 R2 and a minimum client version of Windows Vista.
When you select the provider, hash algorithm, and key length, carefully consider what cryptographic options the applications and devices that you intend to use can support. Although it’s a best practice to select the strongest security options, not all applications and devices can support these. If your support requirements change and you are then able to use the stronger security options, such as migrating to a KSP and a stronger hash algorithm, see Migrating a Certification Authority Key from a Cryptographic Service Provider (CSP) to a Key Storage Provider (KSP).
Allow administrator interaction when the private key is accessed by the CA is an option that is typically used with hardware security modules (HSMs). This allows the cryptographic provider to prompt the user for additional authentication when the private key of the CA is accessed. This option can be used to help prevent unapproved use of the CA and its private key by requiring the administrator to enter a password before every cryptographic operation.
The built-in cryptographic providers support specific key lengths and hash algorithms as described in the following table.
| Cryptographic provider | Key lengths | Hash algorithm |
|---|---|---|
| Microsoft Base Cryptographic Provider v1.0 | — 512 — 1024 — 2048 — 4096 | — SHA1 — MD2 — MD4 — MD5 |
| Microsoft Base DSS Cryptographic Provider | — 512 — 1024 | SHA1 |
| Microsoft Base Smart Card Crypto Provider | — 1024 — 2048 — 4096 | — SHA1 — MD2 — MD4 — MD5 |
| Microsoft Enhanced Cryptographic Provider v1.0 | — 512 — 1024 — 2048 — 4096 | — SHA1 — MD2 — MD4 — MD5 |
| Microsoft Strong Cryptographic Provider | — 512 — 1024 — 2048 — 4096 | — SHA1 — MD2 — MD4 — MD5 |
| RSA#Microsoft Software Key Storage Provider | — 512 — 1024 — 2048 — 4096 | — SHA1 — SHA256 — SHA384 — SHA512 — MD2 — MD4 — MD5 |
| DSA#Microsoft Software Key Storage Provider | — 512 — 1024 — 2048 | SHA1 |
| ECDSA_P256#Microsoft Software Key Storage Provider | 256 | — SHA1 — SHA256 — SHA384 — SHA512 |
| ECDSA_P384#Microsoft Software Key Storage Provider | 384 | — SHA1 — SHA256 — SHA384 — SHA512 |
| ECDSA_P521#Microsoft Software Key Storage Provider | 521 | — SHA1 — SHA256 — SHA384 — SHA512 |
| RSA#Microsoft Smart Card Key Storage Provider | — 1024 — 2048 — 4096 | — SHA1 — SHA256 — SHA384 — SHA512 — MD2 — MD4 — MD5 |
| ECDSA_P256#Microsoft Smart Card Key Storage Provider | 256 | — SHA1 — SHA256 — SHA384 — SHA512 |
| ECDSA_P384#Microsoft Smart Card Key Storage Provider | 384 | — SHA1 — SHA256 — SHA384 — SHA512 |
| ECDSA_P521#Microsoft Smart Card Key Storage Provider | 521 | — SHA1 — SHA256 — SHA384 — SHA512 |
Establish a CA name
Before you configure certification authorities (CAs) in your organization, you should establish a CA naming convention.
You can create a name by using any Unicode character, but you might want to use the ANSI character set if interoperability is a concern. For example, certain types of routers will not be able to use the Network Device Enrollment Service to enroll for certificates if the CA name contains special characters such as an underscore.
If you use non-Latin characters (such as Cyrillic, Arabic, or Chinese characters), your CA name must contain fewer than 64 characters. If you use only non-Latin characters, your CA name can be no more than 37 characters in length.
In Active Directory Domain Services (AD DS), the name that you specify when you configure a server as a CA becomes the common name of the CA, and this name is reflected in every certificate that the CA issues. For this reason, it is important that you do not use the fully qualified domain name for the common name of the CA. This way, malicious users who obtain a copy of a certificate cannot identify and use the fully qualified domain name of the CA to create a potential security vulnerability.
The CA name should not be identical to the name of the computer (NetBIOS or DNS name). Also, you cannot change the name of a server after Active Directory Certificate Services (AD CS) is installed without invalidating all the certificates that are issued by the CA. For additional considerations regarding CA names, see TechNet Wiki article: Considerations for Certification Authority (CA) Names.
To change the server name after AD CS is installed, you must uninstall the CA, change the name of the server, reinstall the CA using the same keys and modify the registry to use the existing CA keys and database. You do not have to reinstall a CA if you rename a domain; however, you will have to reconfigure the CA to support the name change.
Obtain a certificate request
After a root certification authority (CA) has been installed, many organizations will install one or more subordinate CAs to implement policy restrictions on the public key infrastructure (PKI) and to issue certificates to end clients. Using at least one subordinate CA can help protect the root CA from unnecessary exposure. When you install a subordinate CA, you must obtain a certificate from the parent CA.
If the parent CA is online, you can use the Send a certificate request to a parent CA option, and select the parent CA by CA name or computer name.
If the parent CA is offline, you should use the Save a certificate request to file on the target machine option. The procedure for this will be unique to the parent CA. At a minimum, the parent CA should provide a file that contains the subordinate CA’s newly issued certificate, preferably its full certification path.
If you get a subordinate CA certificate that does not include the full certification path, the new subordinate CA that you install must be able to build a valid CA chain when it starts. Do the following to create a valid certification path:
Install the parent CA’s certificate in the Intermediate Certification Authorities certificate store of the computer if the parent CA is not a root CA.
Install the certificates of any other intermediate CA in the chain.
Install the certificate of the root CA into the Trusted Root Certification Authorities store.
These certificates should be installed in the certificate store before you install the CA certificate on the subordinate CA you have just set up.
Verify the validity period
Certificate-based cryptography uses public-key cryptography to protect and sign data. Over time, attackers could obtain data that was protected with the public key and attempt to derive the private key from it. Given enough time and resources, this private key could be compromised, effectively rendering all protected data unprotected. Also the names that are guaranteed by a certificate may need to be changed over time. Because a certificate is a binding between a name and a public key, when either of these change, the certificate should be renewed.
Every certificate has a validity period. After the end of the validity period, the certificate is no longer considered an acceptable or usable credential.
CAs cannot issue certificates that are valid beyond their own validity period. A best practice is to renew the CA certificate when half of its validity period is expired. When installing a CA, you should plan this date and ensure that it is recorded as a future task.
Choose a CA database
As in many databases, the certification authority’s database is a file on the hard drive. In addition to this file, other files serve as the transaction logs, and they receive all modifications to the database before the changes are made. Because these files may be accessed frequently and simultaneously, it is best to keep the database and transaction logs on separate hard drives or high-performance disk configurations, such as striped volumes.
The location of the certificate database and log files are kept in the following registry location:
The registry contains following values:
You can move the certificate database and log files after installation. For information, see article 283193in the Microsoft Knowledge Base.
Configure the CA
After a root or subordinate CA is installed, you must configure the Authority Information Access (AIA) and CRL distribution point (CDP) extensions before the CA issues any certificates. The AIA extension specifies where to find up-to-date certificates for the CA. The CDP extension specifies where to find up-to-date CRLs that are signed by the CA. These extensions apply to all certificates that are issued by that CA.
Configuring these extensions ensures that this information is included in each certificate that the CA issues so that it is available to all clients. This ensures that PKI clients experience the least possible number of failures due to unverified certificate chains or certificate revocations, which can result in unsuccessful VPN connections, failed smart card sign-ins, or unverified email signatures.
As a CA administrator, you can add, remove, or modify CRL distribution points and the locations for CDP and AIA certificate issuance. Modifying the URL for a CRL distribution point only affects newly issued certificates. Previously issued certificates will continue to reference the original location, which is why you should establish these locations before your CA distributes any certificates.
Consider these guidelines when you configure CDP extension URLs:
Avoid publishing delta CRLs on offline root CAs. Because you do not revoke many certificates on an offline root CA, a delta CRL is probably not needed.
Adjust the default LDAP:/// and https:// URL locations on the Extensions tab of the certification authority’s Properties Extension tab according to your needs.
Publish a CRL on an HTTP Internet or extranet location so that users and applications outside the organization can perform certificate validation. You can publish the LDAP and HTTP URLs for CDP locations to enable clients to retrieve CRL data with HTTP and LDAP.
Remember that Windows clients always retrieve the list of URLs in sequential order until a valid CRL is retrieved.
Use HTTP CDP locations to provide accessible CRL locations for clients running non-Windows operating systems.
For more information about CRLs and delta CRLs, see Configuring Certificate Revocation.
Windows PowerShell and certutil support variable numbers (preceded by a percent (%) sign) to help in publishing CDP and AIA locations. The CA’s Properties Extension tab supports bracketed variables. The following table equates the variables between the interfaces and describes their meanings.
| Variable | Extensions tab name | Description |
|---|---|---|
| %1 | The DNS name for the CA computer. If connected to a DNS domain, it is the fully qualified domain name; otherwise, it is the hostname of the computer. | |
| %2 | The NetBIOS name of the CA server | |
| %3 | The name of the CA | |
| %4 | This allows each additional revision of the certificate to have a unique suffix. | |
| %4 | None | Not used |
| %6 | The location of the configuration container in Active Directory Domain Services (AD DS) | |
| %7 | The name of the CA truncated to 32 characters with a hash at the end | |
| %8 | This inserts a suffix on the file name when publishing a CRL to a file or URL location. | |
| %9 | When a delta CRL is published, this replaces the CRLNameSuffix variable with a separate suffix to distinguish the delta CRL from the CRL. | |
| %10 | The object class identifier for CRL distribution points, which is used when publishing to an LDAP URL. | |
| %11 | The object class identifier for a CA, which is used when publishing to an LDAP URL. |
Publish the AIA extension
The AIA extension tells the client computers where they can find the certificate to be verified. This allows the client to confirm whether the certificate can be trusted.
You can configure the AIA extension by using the Certification Authority interface, Windows PowerShell, or the certutil command. The following table describes the options that you can use with the AIA extension by using these methods.
| Interface check box name | Windows PowerShell parameter | Certutil value |
|---|---|---|
| Include in the AIA extension of issued certificate | -AddToCertificateAia | 2 |
| Include in the online certificate status protocol (OCSP) extension | -AddToCertificateOcsp | 32 |
The examples in this section for publishing the AIA extension represent the following scenario:
The domain name is corp.contoso.com.
There is a web server named App1 in the domain.
App1 has a shared folder named PKI that allows the CA Read and Write permissions.
App1 has a DNS CNAME of www and a shared virtual directory named PKI.
The first protocol that client computers should use for the AIA information is HTTP.
The second protocol that client computers should use for the AIA information is LDAP.
The CA that is being configured is an online issuing CA.
OCSP is not in use.
Use the interface to publish the AIA extension
The interface uses the variables and check box names that are described in the previous tables. You can access the interface through the Certification Authority interface. From the contents pane, right-click the CA, click Properties, and then click Extensions. In Select extension, click Authority Information Access (AIA).
Figure 1 AIA extension menu
The locations and settings configured in the user interface are as follows:
Use Windows PowerShell to publish the AIA extension
The following Windows PowerShell commands can be used to configure the AIA extension for the given scenario:
Use certutil to publish the AIA extension
The following certutil command can be used to configure the AIA extension for the given scenario:
Publish the CDP extension
The CDP extension tells client computers where they can find the most recent CRL, so the client can confirm that a particular certificate has not been revoked.
You can configure the CDP extension by using the Certification Authority interface, Windows PowerShell, or the certutil command. The following table describes the options that you can use with the CDP extension by using these methods.
| Interface check box name | Windows PowerShell parameter | Certutil value |
|---|---|---|
| Publish CRLs to this location | -PublishToServer | 1 |
| Include in all CRLs. (Specifies where to publish in Active Directory when publishing manually.) | -AddToCrlCdp | 8 |
| Include in CRLs. (Clients use this to find the delta CRL locations.) | -AddToFreshestCrl | 4 |
| Include in the CDP extension of issued certificates. | -AddToCertificateCdp | 2 |
| Publish Delta CRLs to this location. | -PublishDeltaToServer | 64 |
| Include in the IDP extension of issued CRLs. | -AddToCrlIdp | 128 |
The Issuing Distribution Point (IDP) extension is used by non-Windows clients to verify certificate revocation. The IDP extension allows partitioned CRLs to be deployed when using third-party CAs. Partitioned CRLs allow a third-party CA to publish CRLs with only specific certificate types within each CRL. For example, you can have separate CRLs for end certificates versus CA certificates. Specifically, the following options can be set in the IDP:
The examples in this section for publishing the CDP extension represent the following scenario:
The domain name is corp.contoso.com.
There is a web server named App1 in the domain.
App1 has a shared folder named PKI that allows the CA Read and Write permissions.
App1 has a DNS CNAME of www and a shared virtual directory named PKI.
The first protocol that client computers should use for the CDP information is HTTP.
The second protocol that client computers should use for the CDP information is LDAP.
The CA that is being configured is an online issuing CA.
IDP is not in use.
Use the interface to publish the CDP extension
The interface uses the variables and check box names that are described in the previous tables. You can access the interface through the Certification Authority interface. From the contents pane, right-click the CA, click Properties, and then click Extensions. In Select extension, click CRL Distribution Point (CDP).
Figure 2 CDP extension menu
The locations and settings configured in the interface are as follows:
Publish CRLs to this location
Publish delta CRLs to this location
Include in CRLs. Clients use this to find delta CRL locations.
Include in the CDP extension of issued certificates
Publish CRLs to this location
Publish Delta CRLs to this location
Include in all CRLs. Specifies where to publish in the Active Directory when publishing manually.
Include in the CDP extension of certificates
Use Windows PowerShell to publish the CDP extension
The following Windows PowerShell commands are used to configure the CDP extension for the given scenario:
If you use Windows PowerShell to add CDP paths, existing paths remain in place. The first Windows PowerShell command in the example removes all the existing paths. For more information about using Windows PowerShell to remove CDP paths, see Remove-CACrlDistributionPoint.
Use certutil to publish the CDP extension
The following certutil command configures the CDP extension for the given scenario:
Verify the configuration
To verify the CA configuration, you can run the following commands from Windows PowerShell or a from a Command Prompt window:
You can use the Enterprise PKI View (PKIView.msc) tool to check your AIA and CDP publication configurations. For more information, see the Enterprise PKI.
You can also use the Online Responder role service to check certificate revocation. For more information about Online Responder, see Online Responder Installation, Configuration, and Troubleshooting Guide.
You can’t access OWA or ECP after you install Exchange Server 2016 CU6
Symptoms
After you install and upgrade to Microsoft Exchange Server 2016 Cumulative Update 6 (CU6), you can’t access Outlook Web App (OWA) or Exchange Control Panel (ECP), and you receive the following error message:
🙁 Something went wrong
We can’t get that information right now. Please try again later.
X-ClientId: ClientID
X-FEServer: Exch1
In addition, the following events information is recorded in the Application log of the Exchange server that hosts the mailbox database:
Log Name: Application
Source: MSExchange OAuth
Event ID: 2004
Task Category: Configuration
Level: Warning
Keywords: Classic
User: N/A
Computer: mail.contoso.com
Description:
Unable to find the certificate with thumbprint CertificateValue in the current computer or the certificate is missing private key. The certificate is needed to sign the outgoing token.
Log Name: Application
Source: ASP.NET 4.0.30319.0
Event ID: 1309
Task Category: Web Event
Level: Warning
Keywords: Classic
User: N/A
Description:
Event code: 3005
Event message: An unhandled exception has occurred.
Event ID: EventID
Event sequence: 2
Event occurrence: 1
Event detail code: 0
Application information:
Application domain: /LM/W3SVC/2/ROOT/owa-2- DomainID
Trust level: Full
Application Virtual Path: /owa
Application Path: C:\Program Files\Microsoft\Exchange Server\V15\ClientAccess\owa\
Machine name: Exch1
Process information:
Process ID: 21508
Process name: w3wp.exe
Account name: NT AUTHORITY\SYSTEM
Exception information:
Exception type: TargetInvocationException
Exception message: Exception has been thrown by the target of an invocation.
at System.RuntimeMethodHandle.InvokeMethod(Object target, Object[] arguments, Signature sig, Boolean constructor)
at System.Reflection.RuntimeMethodInfo.UnsafeInvokeInternal(Object obj, Object[] parameters, Object[] arguments)
at System.Reflection.RuntimeMethodInfo.Invoke(Object obj, BindingFlags invokeAttr, Binder binder, Object[] parameters, CultureInfo culture)
at Owin.Loader.DefaultLoader.<>c__DisplayClass12. b__b(IAppBuilder builder)
at Owin.Loader.DefaultLoader.<>c__DisplayClass1. b__0(IAppBuilder builder)
at Microsoft.Owin.Host.SystemWeb.OwinAppContext.Initialize(Action`1 startup)
at Microsoft.Owin.Host.SystemWeb.OwinBuilder.Build(Action`1 startup)
at Microsoft.Owin.Host.SystemWeb.OwinHttpModule.InitializeBlueprint()
at System.Threading.LazyInitializer.EnsureInitializedCore[T](T& target, Boolean& initialized, Object& syncLock, Func`1 valueFactory)
at Microsoft.Owin.Host.SystemWeb.OwinHttpModule.Init(HttpApplication context)
at System.Web.HttpApplication.RegisterEventSubscriptionsWithIIS(IntPtr appContext, HttpContext context, MethodInfo[] handlers)
at System.Web.HttpApplication.InitSpecial(HttpApplicationState state, MethodInfo[] handlers, IntPtr appContext, HttpContext context)
at System.Web.HttpApplicationFactory.GetSpecialApplicationInstance(IntPtr appContext, HttpContext context)
at System.Web.Hosting.PipelineRuntime.InitializeApplication(IntPtr appContext)
Encryption certificate is absent
at Microsoft.Exchange.Security.Authentication.Utility.GetCertificates()
at Microsoft.Exchange.Clients.Owa2.Server.Core.notifications.SignalR.SignalRStartup.Configuration(IAppBuilder app)
Request information:
Request URL: https:// mail.contoso.com: URLID/owa/?bO=1
Request path: /owa/
User host address: UserHostAddressC:\Program Files\Microsoft\Exchange Server\V15\ClientAccess\owa\
User:
Is authenticated: False
Authentication Type:
Thread account name: NT AUTHORITY\SYSTEM
Thread information:
Thread ID: 24
Thread account name: NT AUTHORITY\SYSTEM
Is impersonating: False
Stack trace: at System.RuntimeMethodHandle.InvokeMethod(Object target, Object[] arguments, Signature sig, Boolean constructor)
at System.Reflection.RuntimeMethodInfo.UnsafeInvokeInternal(Object obj, Object[] parameters, Object[] arguments)
at System.Reflection.RuntimeMethodInfo.Invoke(Object obj, BindingFlags invokeAttr, Binder binder, Object[] parameters, CultureInfo culture)
at Owin.Loader.DefaultLoader.<>c__DisplayClass12. b__b(IAppBuilder builder)
at Owin.Loader.DefaultLoader.<>c__DisplayClass1. b__0(IAppBuilder builder)
at Microsoft.Owin.Host.SystemWeb.OwinAppContext.Initialize(Action`1 startup)
at Microsoft.Owin.Host.SystemWeb.OwinBuilder.Build(Action`1 startup)
at Microsoft.Owin.Host.SystemWeb.OwinHttpModule.InitializeBlueprint()
at System.Threading.LazyInitializer.EnsureInitializedCore[T](T& target, Boolean& initialized, Object& syncLock, Func`1 valueFactory)
at Microsoft.Owin.Host.SystemWeb.OwinHttpModule.Init(HttpApplication context)
at System.Web.HttpApplication.RegisterEventSubscriptionsWithIIS(IntPtr appContext, HttpContext context, MethodInfo[] handlers)
at System.Web.HttpApplication.InitSpecial(HttpApplicationState state, MethodInfo[] handlers, IntPtr appContext, HttpContext context)
at System.Web.HttpApplicationFactory.GetSpecialApplicationInstance(IntPtr appContext, HttpContext context)
at System.Web.Hosting.PipelineRuntime.InitializeApplication(IntPtr appContext)
Cause
This issue occurs if the Exchange server Auth certificate that’s used for OAuth signing is missing from the Exchange server. You can run the following command to check whether the certificate is missing:
If the certificate is missing, you will receive the following error message:
A special Rpc error occurs on server Exch1: The certificate with thumbprint CertificateValue was not found.
+ CategoryInfo : NotSpecified: (:) [Get-ExchangeCertificate], InvalidOperationException
+ FullyQualifiedErrorId : [Server=Exch1,RequestId= RequestID] [FailureCategory=Cmdlet-InvalidOperationException] CEA009BC,Microsoft.Exchange.Management.SystemConfigurationTasks.GetExchangeCertificate
Resolution
To fix this issue, install Cumulative Update 7 for Exchange Server 2016 or a later cumulative update for Exchange Server 2016.
Workaround
If your organization has multiple Exchange servers, run the following command in the Exchange Management Shell to confirm if the OAuth certificate is present on other Exchange servers:
If the certificate is present on other Exchange servers, export the certificate and then import it to the Exchange server that has the issue.
If the certificate isn’t present on all Exchange servers in the organization, follow these steps to create and deploy a new OAuth certificate to the Exchange server:
Create a new OAuth certificate by running the following command:
Note Change the value of the DomainName parameter in the example ( contoso.com) to the SMTP domain that’s used in your organization.
Set the created certificate to be used for server authentication by running the following commands:
Restart the Microsoft Exchange Service Host Service.
Either run the IISReset command to restart IIS or run the following commands (in elevated mode) to recycle OWA and ECP APP pools:
Restart-WebAppPool MSExchangeOWAAppPool
Restart-WebAppPool MSExchangeECPAppPool
Note In some environments, it may take an hour for the OAuth certificate to be published.
Status
Microsoft has confirmed that this is a problem in the Microsoft products that are listed in the «Applies to» section.
References
Learn about the terminology that Microsoft uses to describe software updates.
Источники информации:
- http://stackoverflow.com/questions/470523/how-does-ssl-really-work
- http://docs.microsoft.com/en-us/mem/intune/protect/certificates-scep-configure
- http://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/hh831574(v=ws.11)
- http://support.microsoft.com/en-us/topic/you-can-t-access-owa-or-ecp-after-you-install-exchange-server-2016-cu6-88b3fe67-5f97-a8a2-8ed8-70034ff15761


.jpeg)
.jpeg)