Vpn what does it mean
Vpn what does it mean
VPN: ещё раз просто о сложном
Вы сталкивались с ошибкой “Это видео не доступно для просмотра в Вашей стране”? Пробовали заходить на LinkedIn? Подобные ограничения можно обойти с помощью включения VPN на своем девайсе. В последнее время огромное количество людей было вынуждено перейти на дистанционный формат работы и многие работодатели обязали своих сотрудников пользоваться VPN для защищенного доступа к корпоративным сервисам. Сегодня мы постараемся разобраться в том, что такое VPN и как это работает.
Disclaimer: я искала на Хабре базовую статью о VPN, но нашла из базы только часть цикла «Сети для самых маленьких«. Это очень крутая работа, но она сразу не выпадает. Поэтому я решила обобщить все собранные мной определения, знания и структуры, а в начале дать ссылку на «Сети». Надеюсь, это поможет другим пользователям Хабра.
Что такое VPN?
VPN – Virtual Private Network – виртуальная частная сеть.
Это совокупность технологий, позволяющих обеспечить одно или несколько сетевых соединений (логическую сеть) поверх другой сети (например, Интернет).
Расшифровка названия: сеть – объединение нескольких устройств каким-либо видом связи, позволяющее обмениваться информацией. Виртуальная – неосязаемая, не физическая, то есть не важно, по каким именно каналам связи она проложена. Физическая и логическая топологии могут как совпадать, так и отличаться. Частная – в эту сеть не может войти посторонний пользователь, там находятся только те, кому разрешили доступ. В частной сети надо маркировать участников и их трафик, чтобы отличить его от остальной, чужой информации. Также в такой сети обеспечивается защита данных криптографическими средствами, попросту говоря, шифруется.
Приведем еще одно определение: VPN – это сервис, позволяющий защитить приватные данные при пользовании Интернетом.
Зачем нужен VPN?
Для удаленной работы. Например, вы работаете из дома. По VPN вы можете получить доступ к сервисам и документации своей организации, при этом соединение будет более безопасным, данные будет сложно перехватить и расшифровать.
Чтобы объединить разные части одной компании. Офисы могут быть удалены друг от друга на любое расстояние.
Внутри компаний – для объединения и изоляции отделов.
При подключении к Wi-fi в кафе, метро и т.д., чтобы хакеры не могли украсть ваши данные. При пользовании публичной сетью безопасно, разве что просматривать сайты в браузере. А вот если использовать соц.сети, злоумышленник может не только перехватить вашу конфиденциальную информацию, но и использовать ее в своих целях, авторизовавшись в этой самой соц.сети от Вашего имени. Еще хуже, если ему удастся взломать почту. Тогда атаке подвергнутся все приложения, привязанные к этому почтовому ящику. Но самой неприятной может оказаться утечка данных вашей банковской карты, если вы решили перевести кому-то деньги, подключившись к бесплатному Wi-fi.
Для получения доступа к сайтам, которые заблокированы на определенной территории. Приведем пример: Teen Spirit снимает передачу “Орёл и Решка” и продает ее двум телеканалам: российской “Пятнице” и украинскому “Интеру”. Обычно телеканалы на следующий день после выхода премьеры по телевидению, выкладывают выпуск на свой ютуб-канал, чтобы те, кто не успел посмотреть передачу по телевизору, имели возможность сделать это в интернете и, конечно же, для того, чтобы заработать дополнительно на встроенной в ютуб рекламе. На Украине выпуски выходят на день раньше, чем в России. Соответственно, “Интер” выкладывает видео на ютуб, когда по “Пятнице” передачу еще не показали. Поэтому в России в этот день запрещен доступ к этому видео.
Для обеспечения анонимности. Нельзя вычислить, какие сайты вы посещали, каким браузером пользуетесь, где находитесь и т.д. Надобность скрыть свою геолокацию может может возникнуть в путешествиях. Например, в Турции запрещен YouTube и WhatsApp. Значит, просто так зайти в привычные соц.сети не получится, а с VPN это сделать вполне возможно.
Чтобы в браузере оставалась история поиска, на основе которой создается таргетированная реклама
Чтобы сэкономить, например, при покупке авиабилетов. Авиакомпании устанавливают разные цены на одни и те же билеты для покупателей из разных регионов. А VPN позволяет изменить информацию о геолокации.
Как можно пользоваться VPN?
Итак, мы поняли, что VPN – полезный сервис, но как именно можно его включить? Если Вы работаете за компьютером и хотите посетить заблокированный сайт, используя браузер, то можно или установить специальную программу на ПК (так называемый VPN-клиент), или добавить расширение для браузера, или использовать встроенный в Opera VPN. Все эти способы просты в исполнении, но имеют некоторые недостатки. Так, VPN-клиент выдает случайный IP-адрес, то есть нет возможности выбрать страну. Еще один неудобство заключается в необходимости постоянного запуска программы, однако, существуют программы, которые запускаются одновременно с ОС. Теперь рассмотрим следующий способ – добавление расширения для браузера через Webstore. Нужно будет зарегистрироваться, после чего одним кликом можно выбрать страну, к VPN-серверу которой Вы хотите подключиться.
Использование VPN на смартфонах и айфонах реализуется через мобильные приложения. Самые популярные из них – это OpenVPN для Android и Cloak для iOS.
О плюсах VPN и о том, как его можно установить уже Вы прочитали. Самое время поговорить о минусах.
Чем приходится платить за безопасность в Интернете?
Низкая скорость интернета. На дополнительное шифрование требуется время. Также часто трафик проходит большее расстояние, что связано с удаленностью расположения VPN-сервера.
Периодический разрыв VPN-подключения, внезапный выход трафика в публичную сеть. Часто можно не заметить разрыв подключения и утечку данных, также VPN-соединение может не восстанавливаться автоматически, что не удобно. Во современных ОС на базе Windows предусмотрена функция VPN Reconnect. Если ее нет, то придется использовать особые программы или специальные настройки маршрутизации, которые контролируют VPN-соединение и в случае его разрыва сначала блокируют передаваемую информацию, закрывают приложения, потом обновляют VPN-подключение.
К сожалению, IPv6 почти никогда не поддерживается VPN. Следовательно, когда в публичной сети используется IPv6, и в интернет-ресурсе он также поддерживается, трафик пойдет по умолчанию по открытой IPv6 сети. Чтобы такого не произошло можно просто отключить IPv6 в ОС.
DNS-протечки: на практике часто DNS-запросы обрабатываются DNS-серверами публичной сети (а не виртуальной, защищенной). В случае их некорректного ответа можно получить поддельный адрес запрашиваемого домена. Так, ничего не подозревающие пользователи могут быть перенаправлены, например, на сайты мошеннических онлайн-банков. Также по DNS-серверам можно определить примерную геолокацию и интернет-провайдера пользователя.
Присутствуют также разнообразные юридические аспекты. Во-первых, это отличия в законодательстве разных государств. VPN-клиент и VPN-сервер часто находятся в разных странах. Также трафик может проходить через третью страну транзитом. Таким образом существует возможность сохранить себе копию передаваемых данных для дальнейшей расшифровки и изучения.
Существует не только вопрос что шифровать, но и как. Далеко не все криптографические средства разрешены. Из-за этого производители сетевого оборудования (в том числе для организаций VPN) при экспорте в другие страны вынуждены отключать в своей продукции ряд алгоритмов шифрования, а также уменьшать максимально возможную длину ключа.
Проблема кроется еще и в том, что сами мировые стандарты шифрования могут быть уязвимыми. Так, в 2013 году NIST (The National Institute of Standards and Technology – организация, утверждающая стандарты шифрования в США) обвинили в том, что он разрешил включить в новый стандарт уязвимую версию генератора псевдослучайных чисел. Это позволило сильно упростить расшифровку информации, защищенной с применением этого генератора. Более того, составителей стандартов нередко обвиняют в сознательном усложнении описаний стандартов.
Как работает VPN?
Соединение VPN – это, так называемый, “туннель” между компьютером пользователя и компьютером-сервером. Каждый узел шифрует данные до их попадания в “туннель”.
Вы подключаетесь к VPN, система идентифицирует вашу сеть и начинает аутентификацию (сравнивает введенный пароль с паролем в своей базе данных).
Далее сервер Вас авторизует, то есть предоставляет право на выполнение определенных действий: чтение почты, интернет-серфинг и т.д. После установления соединения весь трафик передается между вашим ПК и сервером в зашифрованном виде. Ваш ПК имеет IP-адрес, предоставленный интернет-провайдером. Этот IP блокирует доступ к некоторым сайтам. VPN сервер меняет ваш IP на свой. Уже с VPN-сервера все данные передаются к внешним ресурсам, которые вы запрашиваете. Теперь можно просматривать любые ресурсы и не быть отслеженным.
Однако, следует помнить, что не вся информация шифруется. У разных VPN-провайдеров могут отличаться такие характеристики как степень шифрования, сокрытие факта подключения к серверу, хранение логов (журнал, в который сохраняется информация о посещаемых сайтах, реальный IP адреси т.п.) и сотрудничество при выдаче информации третьим лицам.
Если VPN-провайдер вообще не записывает логи, то передавать третьим лицам просто нечего. А сокрытие факта подключения к серверу – уже более редкая услуга. При некорректном подключении или резком разрыве соединения может произойти утечка части данных. Решить проблему поможет технология Multihop VPN, которая предполагает соединение с сайтом сразу через несколько серверов.
Рассмотрим популярные VPN:
PPTP – Point-to-Point Tunneling Protocol
+ поддерживается всеми ОС
+ не требует много вычислительных мощностей
— плохая защищенность. Методы шифрования устарели, плохая архитектура, есть ошибки в реализации протокола от Microsoft. Нет шифрования по умолчанию, на взлом требуется менее суток.
Используется, когда защита данных не очень важна или когда нет других вариантов.
L2TP – Layer 2 Tunneling Protocol
+ более эффективен для построения виртуальных сетей
— более требователен к вычислительным ресурсам
— не предполагает шифрования по умолчанию
Работает совместно с другими протоколами, чаще всего IPSec.
Используется интернет-провайдерами и корпоративными пользователями.
IPSec – Internet Protocol Security – группа протоколов и стандартов для безопасных соединений.
— сложен в настройке (следовательно, снижение защиты, если настроить неправильно)
— требует много вычислительных ресурсов
+ этот недостаток компенсируется путем аппаратного ускорения алгоритма шифрования АЕС
Часто используется совместно с другими технологиями.
SSL – Secure Sockets Layer & TLS – Transport Layer Security – группа методов, включающая в себя протоколы SSL и TLS и другие методы защиты.
+ беспрепятственно пропускаются большинством публичных сетей
— довольно низкая производительность
— сложность в настройке, необходимость установки дополнительного ПО
используется на веб-сайтах, URL которых начинается с https (там еще виден зеленый замочек)
некоторые реализации: OpenVPN, Microsoft SSTP.
+ OpenVPN имеет открытый код, реализован практически для всех платформ, считается очень надежным.
Заключение
VPN – комплекс технологий, позволяющих создать логическую сеть поверх физической. Используется для обеспечения защиты трафика от перехвата злоумышленниками и безопасной деятельности в интернете. VPN открывает доступ к заблокированным ресурсам, так что многие готовы мириться с более низкой скоростью интернета и возможными логами программ. Хотя VPN использует довольно надежные алгоритмы шифрования, включение VPN-клиента на вашем ПК не гарантирует 100% сохранности конфиденциальной информации, поэтому следует внимательно отнестись к выбору VPN-провайдера.
What is a VPN?
Posted on November 5th, 2020 by Douglas Crawford in Privacy & Security.
An almost daily drumbeat of data breaches and online privacy violations has fueled public interest in VPN services such as Proton VPN. This article explains what VPNs are, what they do, and whether you need one. Our sister article, How does a VPN work?, provides a more detailed and technical overview of what is going on under the hood.
What is a VPN?
A virtual private network (VPN) is a suite of technologies, the primary aim of which is to improve your privacy when using the internet. It connects your computer, smartphone, or tablet to another computer, called a VPN server, via an encrypted “tunnel” that protects your data from prying eyes.
Benefits of a VPN
This deceptively simple setup is very useful. A VPN:
All mass surveillance systems in the world rely on ISPs logging their users’ browsing histories and making these logs available to government agencies. Because a VPN prevents your ISP from seeing the information you send and receive online, it therefore also:
Almost as a by-product of how VPNs work, using a VPN offers important additional advantages. Although these could be viewed as side effects, they are the main reason many people use a VPN:
A VPN is, therefore, something of a Swiss army knife among internet tools and one that everyone should have in their toolkit.
Why you need a VPN
Privacy
From your ISP and government
A VPN encrypts the connection between your device and the VPN server. This prevents your ISP from seeing the contents of your data, including destination data that can usually tell it which websites and other resources you connect to on the internet.
Your VPN provider also handles DNS translation, which is normally performed and logged by your ISP. DNS is basically like a big phone book that translates the easy-to-remember URLs that people use into the numbers computers really use to identify websites and other internet resources.
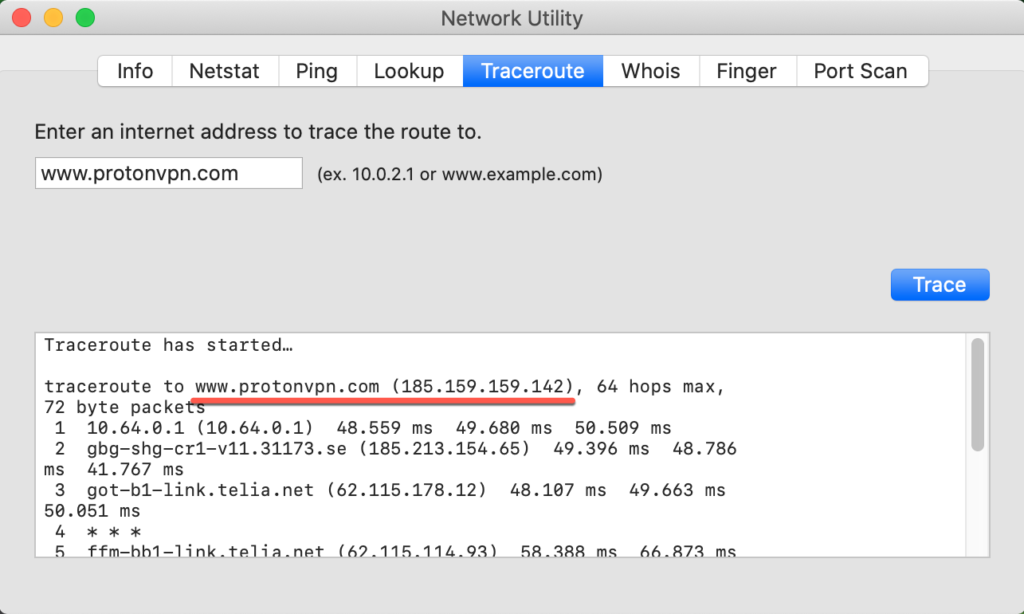
DNS, for example, translates the URL www.protonvpn.com into its corresponding IP address of 185.159.159.142. Keeping logs of DNS translation is the main way that most ISPs keep tabs on what their customers do online.
The upshot of all this is that using a VPN prevents your ISP from knowing what you do on the internet. It can’t see your data, and it can’t see which websites you visit.
As we have already touched on, what your ISP doesn’t know, your government and global surveillance bodies such as the NSA and GCHQ are also unlikely to know. A VPN prevents your browsing history from being caught up in untargeted dragnet mass surveillance programs that invariably rely on the logs kept by your ISP.
A VPN will not, of course, prevent targeted surveillance, in which an adversary (such as your government) is willing to expend time and resources spying on you as a known individual.
From websites
The VPN server acts as a shield that blocks the “view” both ways. Your ISP can’t see which websites you connect to (just the VPN server), and websites you connect to can’t see your real unique IP address (again, they just see the IP address of the VPN server).
A VPN, therefore, stops the easiest-to-perform and most invasive kind of web tracking. Be aware, however, that preventing other common forms of web tracking, such as cookies and browser fingerprinting, is beyond the scope of what a VPN can do.
A VPN should, therefore, be used in combination with browser-based anti-tracking solutions to provide a wide-spectrum defense against the multitude of threats to our privacy that the internet facilitates.
Security
WiFi connections on insecure public hotspots, such as the one you use in an airport lounge or your local cafe, can be easily hacked by criminals who wish to steal your data. It is also very easy to accidentally connect to a fake “evil twin” hotspot with a name like “airport wifi,” which is a sneaky tactic commonly used by criminal hackers to access your data.
Using a VPN protects you from public WiFi hackers of all stripes since all data between your device and the VPN is securely encrypted. It should be said, though, that the huge uptake of HTTPS over the last years (please see How does a VPN work? for more details) means that WiFi hackers are simply not the threat they once were.
A greater threat these days comes from “legitimate” WiFi router hosts. Many public WiFi hotspots are commercial enterprises, something made clear when you are forced to agree to a lengthy set of terms and conditions before you are allowed to use the service. What these terms and conditions boil down to is that the WiFi host can monitor your internet activity to sell your browsing history to advertising and analytics companies.
There has also been growing concern about the possibility of Airbnb hosts and the like abusing their positions of trust to spy on guests’ internet activities. In all such cases, a VPN will protect you from these invasive practices.
Defeat censorship
VPNs are highly effective at defeating censorship efforts. If your country blocks content, then simply connect to a VPN server located somewhere the content is not blocked. If your school, college, or workplace blocks content, connecting to any VPN server will bypass that block.
If using a VPN to bypass censorship, please carefully consider the risks involved if you are caught. Using OpenVPN in TLS mode can be highly effective at hiding VPN traffic as regular HTTPS traffic, but it can be detected by the advanced deep packet inspection (DPI) techniques used by some governments.
It is also possible that your organization or government has blacklisted IP addresses known to belong to VPN services, in which case trying to connect to a blocked VPN server address could bring up a red flag. It’s also worth remembering that your boss might simply just walk into your room at the wrong moment.
Although VPNs can defeat most censorship efforts, it is possible for a powerful enough adversary (such as the Chinese government) to implement blocks that even a VPN cannot overcome. In such cases, using the Tor network with unlisted Tor servers and/or Tor bridges that use pluggable transports to evade deep packet inspection techniques may be the most effective solution.
Streaming
For all the freedom-enabling privacy benefits a VPN can offer, one of the most popular uses for VPNs is to stream media content that only is supposed to be available in certain countries.
The world-famous BBC iPlayer, for example, is available for free to anyone who appears to be in the UK. And US residents enjoy a much larger Netflix catalog than customers in other countries, despite most people paying a similar monthly subscription cost no matter where they are located.
A VPN allows you to “spoof” your location in order to pretend to be in a certain country, and thus access services only available in that country from anywhere in the world.
Most such services do still require a valid subscription, but Netflix customers (for example) can log in to regional versions of the service (including the US one) using valid accounts that are registered anywhere.
Proton VPN users with Plus or Visionary plans can access a wide selection of popular streaming sites using our service.
P2P file sharing
As with websites you visit, a VPN will hide your real IP address from peers when file sharing using the BitTorrent protocol. This makes using a VPN an essential precaution for torrenters. A VPN is also useful for accessing torrent sites that may be blocked by your ISP.
Yes and no. Yes, because it stops your ISP from knowing what you do online, and because it stops websites you visit from knowing your real IP address. Using a VPN can, therefore, provide a high level of privacy when online.
No, because the VPN provider knows who you are and is able to monitor and log your activity. Good VPN services such as Proton VPN take great care to mitigate this issue by maintaining a strict no-logs policy. (Our latest security audit results confirm our no logs policy.)
Yes. In fact, using a VPN on your mobile device is as important as using on your desktop system. Proton VPN offers apps for both Android and iOS/iPadOS devices.
No logs VPNs such as Proton VPN keep no logs of users’ activities that might at a future point compromise their privacy.
Other than payment details, which are never tied to users’ online activities, Proton VPN keeps no logs whatsoever. And under Swiss law, we cannot be compelled to start logging.
Proton VPN can unblock a wide selection of popular streaming services, including Netflix and Hulu, by connecting to our Plus servers. You still need a valid account with these services to access their content.
A Netflix account registered anywhere in the world is sufficient to access an unblocked Netflix site anywhere else in the world. To access Hulu, however, you need an account that is registered in the United States.
Services such as BBC iPlayer and ALL4 allow anyone to register for free from an unblocked UK IP address.
A kill switch helps to protect your privacy by disabling your internet connection if there is a problem with the VPN connection. This ensures that you do not unknowingly or accidentally connect to the internet without the VPN running properly.
Proton VPN features kill switches in its Windows, macOS, Linux, and Android apps. Apple’s restrictive developer guidelines mean that it is not possible to implement a kill switch in iOS, but our iOS app has an “Always-on” feature instead, that will swiftly and automatically reconnect you if you disconnect.
We can’t speak for all VPN services, but Proton VPN keeps no logs that can compromise your privacy, is based in Switzerland, home of some of the strongest data privacy laws in the world, uses only the strongest VPN protocols and encryption suites possible, and makes the source code of all our apps freely available for anyone to audit.
We have commissioned professional third-party audits of all our apps, the results of which are publicly available.
Again, we can only speak for ourselves. Proton VPN uses the OpenVPN and IKEv2 protocols for its apps, which experts agree are the most secure VPN protocols yet devised. We also implement these at their strongest encryption settings.
Our open source apps feature kill switches to protect you against VPN dropouts, and built-in DNS and IPv6 leak protection ensure there is no possibility your privacy can be compromised.
Our servers are all “hardened” with multiple security layers and failsafes, in addition to using robust physical security measures. Where security is of paramount importance, you might like to consider using our special Secure Core service for additional protection.
Many routers these days feature a built-in VPN client. Alternatively, you can replace the firmware that comes with just about any router with an open source alternative such as DD-WRT that supports VPN connections.
The advantage of using a VPN on your router is that all devices which connect to the router are protected by the VPN. The router also counts as just one VPN connection, no matter how many devices you connect to it.
If you have a dual-band router, you can set up the VPN on one band and connect devices that you don’t want to use the VPN on to the other. Proton VPN has detailed VPN router setup guides for a number of popular routers.
Final thoughts
A VPN provides privacy while surfing the net: from your ISP, from your government, and from websites you visit. Millions of people around the world use VPN services as an invaluable tool to defeat censorship and access the open internet. It also protects you from “free” WiFi providers.
Proton VPN is a community-driven VPN service that places the privacy of our users first and foremost. We keep no logs, and what little data we do store is protected by Swiss data protection laws. All of our apps are open source and independently audited, and we support journalists and activists in the struggle for a free and open internet.
You can follow us on social media to stay up to date on the latest Proton VPN releases:
To get a free Proton Mail encrypted email account, visit protonmail.com.
Douglas Crawford
Douglas has worked for many years as a technology writer in the cyberprivacy and cybersecurity sector. He is now very pleased to work for a company with a mission that he passionately believes in.
What is VPN? How It Works, Types of VPN
VPN stands for «Virtual Private Network» and describes the opportunity to establish a protected network connection when using public networks. VPNs encrypt your internet traffic and disguise your online identity. This makes it more difficult for third parties to track your activities online and steal data. The encryption takes place in real time.
How does a VPN work?
A VPN hides your IP address by letting the network redirect it through a specially configured remote server run by a VPN host. This means that if you surf online with a VPN, the VPN server becomes the source of your data. This means your Internet Service Provider (ISP) and other third parties cannot see which websites you visit or what data you send and receive online. A VPN works like a filter that turns all your data into «gibberish». Even if someone were to get their hands on your data, it would be useless.
What are the benefits of a VPN connection?
A VPN connection disguises your data traffic online and protects it from external access. Unencrypted data can be viewed by anyone who has network access and wants to see it. With a VPN, hackers and cyber criminals can’t decipher this data.
Disguising your whereabouts : VPN servers essentially act as your proxies on the internet. Because the demographic location data comes from a server in another country, your actual location cannot be determined. In addition, most VPN services do not store logs of your activities. Some providers, on the other hand, record your behavior, but do not pass this information on to third parties. This means that any potential record of your user behavior remains permanently hidden.
Secure data transfer: If you work remotely, you may need to access important files on your company’s network. For security reasons, this kind of information requires a secure connection. To gain access to the network, a VPN connection is often required. VPN services connect to private servers and use encryption methods to reduce the risk of data leakage.
Why should you use a VPN connection?
Your ISP usually sets up your connection when you connect to the internet. It tracks you via an IP address. Your network traffic is routed through your ISP’s servers, which can log and display everything you do online.
Your ISP may seem trustworthy, but it may share your browsing history with advertisers, the police or government, and/or other third parties. ISPs can also fall victim to attacks by cyber criminals: If they are hacked, your personal and private data can be compromised.
This is especially important if you regularly connect to public Wi-Fi networks. You never know who might be monitoring your internet traffic and what they might steal from you, including passwords, personal data, payment information, or even your entire identity.
What should a good VPN do?
You should rely on your VPN to perform one or more tasks. The VPN itself should also be protected against compromise. These are the features you should expect from a comprehensive VPN solution:
The history of VPNs
Since humans have been using the internet, there has been a movement to protect and encrypt internet browser data. The US Department of Defense already got involved in projects working on the encryption of internet communication data back in the 1960s.
The predecessors of the VPN
Their efforts led to the creation of ARPANET (Advanced Research Projects Agency Network), a packet switching network, which in turn led to the development of the Transfer Control Protocol/Internet Protocol (TCP/IP).
The TCP/IP had four levels: Link, internet, transport and application. At the internet level, local networks and devices could be connected to the universal network – and this is where the risk of exposure became clear. In 1993, a team from Columbia University and AT&T Bell Labs finally succeeded in creating a kind of first version of the modern VPN, known as swIPe: Software IP encryption protocol.
In the following year, Wei Xu developed the IPSec network, an internet security protocol that authenticates and encrypts information packets shared online. In 1996, a Microsoft employee named Gurdeep Singh-Pall created a Peer-to-Peer Tunneling Protocol (PPTP).
Early VPNs
Contiguous to Singh-Pall developing PPTP, the internet was growing in popularity and the need for consumer-ready, sophisticated security systems emerged. At that time, anti-virus programs were already effective in preventing malware and spyware from infecting a computer system. However, people and companies also started demanding encryption software that could hide their browsing history on the internet.
The first VPNs therefore started in the early 2000s, but were almost exclusively used by companies. However, after a flood of security breaches, especially in the early 2010s, the consumer market for VPNs started to pick up.
VPNs and their current use
According to the GlobalWebIndex, the number of VPN users worldwide increased more than fourfold between 2016 and 2018. In countries such as Thailand, Indonesia and China, where internet use is restricted and censored, one in fiveinternet users uses a VPN. In the USA, Great Britain and Germany, the proportion of VPN users is lowerat around 5%, but is growing.
One of the biggest drivers for VPN adoption in recent years has been the increasing demand for content with geographical access restrictions. For example, video streaming services such as Netflix or YouTube make certain videos available only in certain countries. With contemporary VPNs, you can encrypt your IP address so that you appear to be surfing from another country, enabling you to access this content from anywhere.
Here’s how to surf securely with a VPN
A VPN encrypts your surfing behavior, which can only be decoded with the help of a key. Only your computer and the VPN know this key, so your ISP cannot recognize where you are surfing. Different VPNs use different encryption processes, but generally function in three steps:
What kind of VPNs are there?
There are many different types of VPNs, but you should definitely be familiar with the three main types:
SSL VPN
Often not all employees of a company have access to a company laptop they can use to work from home. During the corona crisis in Spring 2020, many companies faced the problem of not having enough equipment for their employees. In such cases, use of a private device (PC, laptop, tablet, mobile phone) is often resorted to. In this case, companies fall back on an SSL-VPN solution, which is usually implemented via a corresponding hardware box.
The prerequisite is usually an HTML-5-capable browser, which is used to call up the company’s login page. HTML-5 capable browsers are available for virtually any operating system. Access is guarded with a username and password.
Site-to-site VPN
A site-to-site VPN is essentially a private network designed to hide private intranets and allow users of these secure networks to access each other’s resources.
A site-to-site VPN is useful if you have multiple locations in your company, each with its own local area network (LAN) connected to the WAN (Wide Area Network). Site-to-site VPNs are also useful if you have two separate intranets between which you want to send files without users from one intranet explicitly accessing the other.
Site-to-site VPNs are mainly used in large companies. They are complex to implement and do not offer the same flexibility as SSL VPNs. However, they are the most effective way to ensure communication within and between large departments.
Client-to-Server VPN
Connecting via a VPN client can be imagined as if you were connecting your home PC to the company with an extension cable. Employees can dial into the company network from their home office via the secure connection and act as if they were sitting in the office. However, a VPN client must first be installed and configured on the computer.
This involves the user not being connected to the internet via his own ISP, but establishing a direct connection through his/her VPN provider. This essentially shortens the tunnel phase of the VPN journey. Instead of using the VPN to create an encryption tunnel to disguise the existing internet connection, the VPN can automatically encrypt the data before it is made available to the user.
This is an increasingly common form of VPN, which is particularly useful for providers of insecure public WLAN. It prevents third parties from accessing and compromising the network connection and encrypts data all the way to the provider. It also prevents ISPs from accessing data that, for whatever reason, remains unencrypted and bypasses any restrictions on the user’s internet access (for instance, if the government of that country restricts internet access).
The advantage of this type of VPN access is greater efficiency and universal access to company resources. Provided an appropriate telephone system is available, the employee can, for example, connect to the system with a headset and act as if he/she were at their company workplace. For example, customers of the company cannot even tell whether the employee is at work in the company or in their home office.
How do I install a VPN on my computer?
Before installing a VPN, it is important to be familiar with the different implementation methods:
VPN client
Software must be installed for standalone VPN clients. This software is configured to meet the requirements of the endpoint. When setting up the VPN, the endpoint executes the VPN link and connects to the other endpoint, creating the encryption tunnel. In companies, this step usually requires the entry of a password issued by the company or the installation of an appropriate certificate. By using a password or certificate, the firewall can recognize that this is an authorized connection. The employee then identifies him/herself by means of credentials known to him/her.
Browser extensions
VPN extensions can be added to most web browsers such as Google Chrome and Firefox. Some browsers, including Opera, even have their own integrated VPN extensions. Extensions make it easier for users to quickly switch and configure their VPN while surfing the internet. However, the VPN connection is only valid for information that is shared in this browser. Using other browsers and other internet uses outside the browser (e.g. online games) cannot be encrypted by the VPN.
While browser extensions are not quite as comprehensive as VPN clients, they may be an appropriate option for occasional internet users who want an extra layer of internet security. However, they have proven to be more susceptible to breaches. Users are also advised to choose a reputable extension, as data harvesters may attempt to use fake VPN extensions. Data harvesting is the collection of personal data, such as what marketing strategists do to create a personal profile of you. Advertising content is then personally tailored to you.
Router VPN
If multiple devices are connected to the same internet connection, it may be easier to implement the VPN directly on the router than to install a separate VPN on each device. A router VPN is especially useful if you want to protect devices with an internet connection that are not easy to configure, such as smart TVs. They can even help you access geographically restricted content through your home entertainment systems.
A router VPN is easy to install, always provides security and privacy, and prevents your network from being compromised when insecure devices log on. However, it may be more difficult to manage if your router does not have its own user interface. This can lead to incoming connections being blocked.
Company VPN
A company VPN is a custom solution that requires personalized setup and technical support. The VPN is usually created for you by the company’s IT team. As a user, you have no administrative influence from the VPN itself and your activities and data transfers are logged by your company. This allows the company to minimize the potential risk of data leakage. The main advantage of a corporate VPN is a fully secure connection to the company’s intranet and server, even for employees who work outside the company using their own internet connection.
Can I also use a VPN on my smartphone or other devices?
Is a VPN really so secure?
Once the malware has found its way onto your device, it can steal or damage your data, whether you are running a VPN or not. It is therefore important that you use a VPN together with a comprehensive anti-virus program to ensure maximum security.
Selecting a secure VPN provider
It is also important that you choose a VPN provider that you can trust. While your ISP cannot see your internet traffic, your VPN provider can. If your VPN provider is compromised, so are you. For this reason, it is crucial that you choose a trusted VPN provider to ensure both the concealment of your internet activities and ensure the highest level of security.
How to install a VPN connection on your smartphone
As already mentioned, there are also VPN connections for Android smartphones and iPhones. Fortunately, smartphone VPN services are easy to use and generally include the following:
Remember that only internet data is encrypted. Anything that does not use a cellular or Wi-Fi connection will not be transmitted over the internet. As a result, your VPN will not encrypt your standard voice calls or texts.
Conclusion
A VPN connection establishes a secure connection between you and the internet. Via the VPN, all your data traffic is routed through an encrypted virtual tunnel. This disguises your IP address when you use the internet, making its location invisible to everyone. A VPN connection is also secure against external attacks. That’s because only you can access the data in the encrypted tunnel – and nobody else can because they don’t have the key. A VPN allows you to access regionally restricted content from anywhere in the world. Many streaming platforms are not available in every country. You can still access them using the VPN. VPN solutions from Kaspersky are available for both Windows PCs and Apple Macs.
There are now also many providers of VPN connections for smartphones which keep mobile data traffic anonymous. You can find certified providers in the Google Play Store or the iOS App Store. However, remember that only your data traffic on the internet is anonymized and protected by using a VPN. The VPN connection does not protect you from hacker attacks, Trojans, viruses or other malware. You should therefore rely on an additional trusted anti-virus software.
What Is a VPN, and Why Would I Need One?
Chris Hoffman is Editor-in-Chief of How-To Geek. He’s written about technology for over a decade and was a PCWorld columnist for two years. Chris has written for The New York Times and Reader’s Digest, been interviewed as a technology expert on TV stations like Miami’s NBC 6, and had his work covered by news outlets like the BBC. Since 2011, Chris has written over 2,000 articles that have been read more than one billion times—and that’s just here at How-To Geek. Read more.
Justin Duino is the Reviews Director at How-To Geek (and LifeSavvy Media as a whole). He has spent the last decade writing about Android, smartphones, and other mobile technology. In addition to his written work, he has also been a regular guest commentator on CBS News and BBC World News and Radio to discuss current events in the technology industry. Read more.
A VPN, or Virtual Private Network, allows you to create a secure connection to another network over the Internet. VPNs can be used to access region-restricted websites, shield your browsing activity from prying eyes on public Wi-Fi, and more.
These days VPNs are really popular, but not for the reasons they were originally created. They originally were just a way to connect business networks together securely over the internet or allow you to access a business network from home.
VPNs essentially forward all your network traffic to the network, which is where the benefits — like accessing local network resources remotely and bypassing Internet censorship — all come from. Most operating systems have integrated VPN support.
What Is a VPN and How Does It Help Me?
In very simple terms, a VPN connects your PC, smartphone, or tablet to another computer (called a server) somewhere on the internet, and allows you to browse the internet using that computer’s internet connection. So if that server is in a different country, it will appear as if you are coming from that country, and you can potentially access things that you couldn’t normally.
So how does this help you? Good question! You can use a VPN to:
Many people these days are using a VPN for torrenting or bypassing geographic restrictions to watch content in a different country. They are still very useful for protecting yourself while working at a coffee shop, but that’s hardly the only use anymore.
| Everything You Need to Know About VPNs | |
| Which Is the Best VPN? | Best VPN for You | ExpressVPN vs. NordVPN | Surfshark vs. ExpressVPN | Surfshark vs. NordVPN |
| Additional VPN Guides | What’s a VPN? | How to Choose a VPN | Using a VPN With Netflix | Best VPN Protocol | The 6 VPN Features That Matter Most | What Is a VPN Killswitch? | 5 Signs a VPN Isn’t Trustworthy | Should You Use a VPN? | VPN Myths Debunked |
How Do You Get a VPN, and Which One Should You Choose?
Depending on your needs, you can either use a VPN from your workplace, create a VPN server yourself, or sometimes host one out of your house — but realistically the vast majority of people are just looking for something to protect them while torrenting or help them watch some media online that they can’t seem to access from their country.
The easiest thing to do is simply head to one of these sites, sign up, and download the VPN client for your Windows PC, Mac, Android, iPhone, or iPad. It’s as easy as that.
All of them have free trials, so you can easily get your money back if you change your mind.
ExpressVPN
ExpressVPN is fast, easy to use, and cheap. Many of us here at How-To Geek have used and trusted it for years. We highly recommend it.
TunnelBear
TunnelBear is an easy-to-use VPN with a limited free plan. It’s especially great if you only occasionally need a VPN.
How Does a VPN Work?
When you connect your computer (or another device, such as a smartphone or tablet) to a VPN, the computer acts as if it’s on the same local network as the VPN. All your network traffic is sent over a secure connection to the VPN. Because your computer behaves as if it’s on the network, this allows you to securely access local network resources even when you’re on the other side of the world. You’ll also be able to use the Internet as if you were present at the VPN’s location, which has some benefits if you’re using public Wi-Fi or want to access geo-blocked websites.
When you browse the web while connected to a VPN, your computer contacts the website through the encrypted VPN connection. The VPN forwards the request for you and forwards the response from the website back through the secure connection. If you’re using a USA-based VPN to access Netflix, Netflix will see your connection as coming from within the USA.
Other Example Uses for VPNs
VPNs are a fairly simple tool, but they can be used to do a wide variety of things:
Using a Corporate VPN in Windows
Connecting to a VPN is fairly simple. In Windows, press the Windows key, type VPN, and click the Set up a virtual private network (VPN) connection option. (If you use Windows, you’ll have to click the Settings category after searching.) Use the wizard to enter the address and login credentials of the VPN service you want to use. You can then connect to and disconnect from VPNs using the network icon in the system tray — the same one where you manage the Wi-Fi networks you’re connected to.
Our VPN Recommendations
If you’re just getting started with VPNs and want the best VPN for using on public Wi-Fi hotspots or accessing region-restricted websites, there are a few good, simple options. We like ExpressVPN because they have great speeds and a lot more functionality than average including clients for almost any device—you can even get a router pre-installed with their VPN client.
There are other VPN products on the market, of course—we also like StrongVPN for all the configuration options it provides—and for limited use, TunnelBear has a free option limited to 500MB — which is great if you just need a client briefly.
You may also be interested in setting up a VPN on your own server, which you can do with Tomato, OpenWRT, or on Linux. Of course, this won’t allow you to access geo-blocked websites — unless you’re traveling outside the country and accessing your own network remotely.
A virtual private network, or VPN, is an encrypted connection over the Internet from a device to a network. The encrypted connection helps ensure that sensitive data is safely transmitted. It prevents unauthorized people from eavesdropping on the traffic and allows the user to conduct work remotely. VPN technology is widely used in corporate environments.
Contact Cisco
Secure your remote workforce, fast
If you’re looking to increase protection for your remote employees so they can work from any device, at any time, from any location, get started with the Cisco Secure Remote Worker solution.
How does a virtual private network (VPN) work?
A VPN extends a corporate network through encrypted connections made over the Internet. Because the traffic is encrypted between the device and the network, traffic remains private as it travels. An employee can work outside the office and still securely connect to the corporate network. Even smartphones and tablets can connect through a VPN.
What is secure remote access?
Secure remote access provides a safe, secure way to connect users and devices remotely to a corporate network. It includes VPN technology that uses strong ways to authenticate the user or device. VPN technology is available to check whether a device meets certain requirements, also called a device’s posture, before it is allowed to connect remotely.
Is VPN traffic encrypted?
Yes, traffic on the virtual network is sent securely by establishing an encrypted connection across the Internet known as a tunnel. VPN traffic from a device such as a computer, tablet, or smartphone is encrypted as it travels through this tunnel. Offsite employees can then use the virtual network to access the corporate network.









